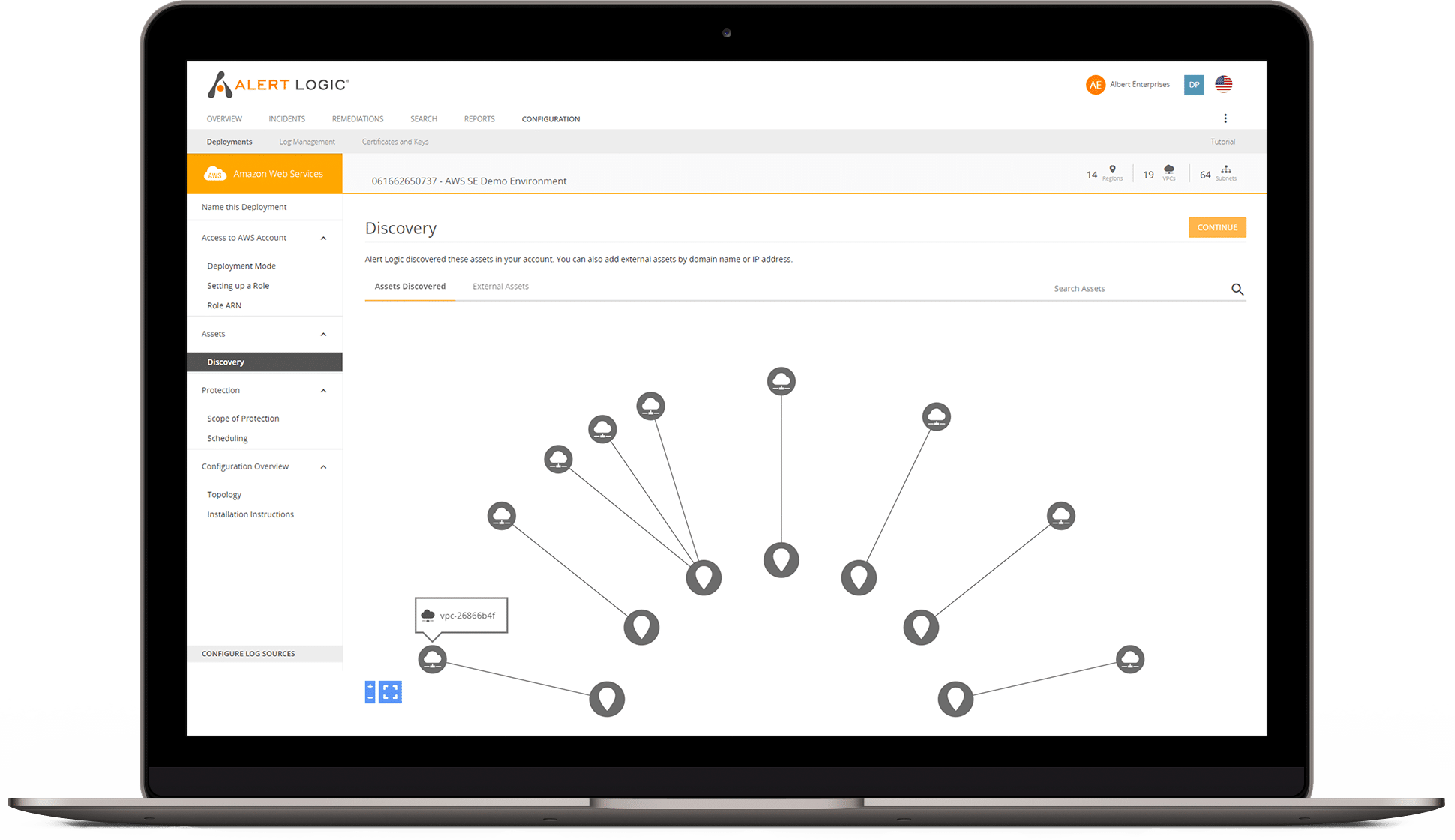
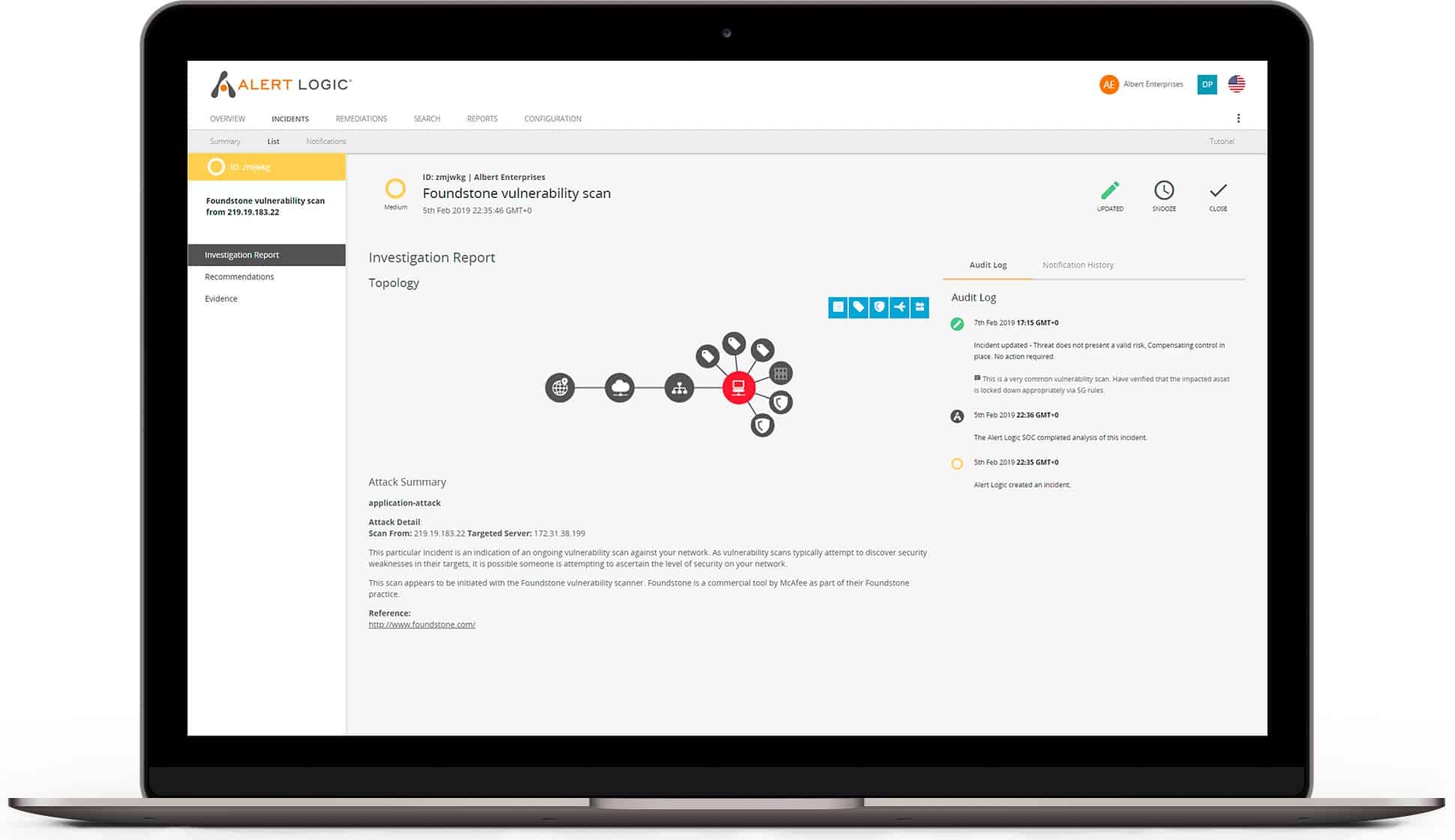
Alert Logic’s network discovery scanner continuously gathers detailed information about the quantity, location, and condition of assets across your enterprise, whether in the cloud, on-premises, or in hybrid environments. This streamlined discovery process is fully managed for you, helping you maintain accurate IT asset visibility.
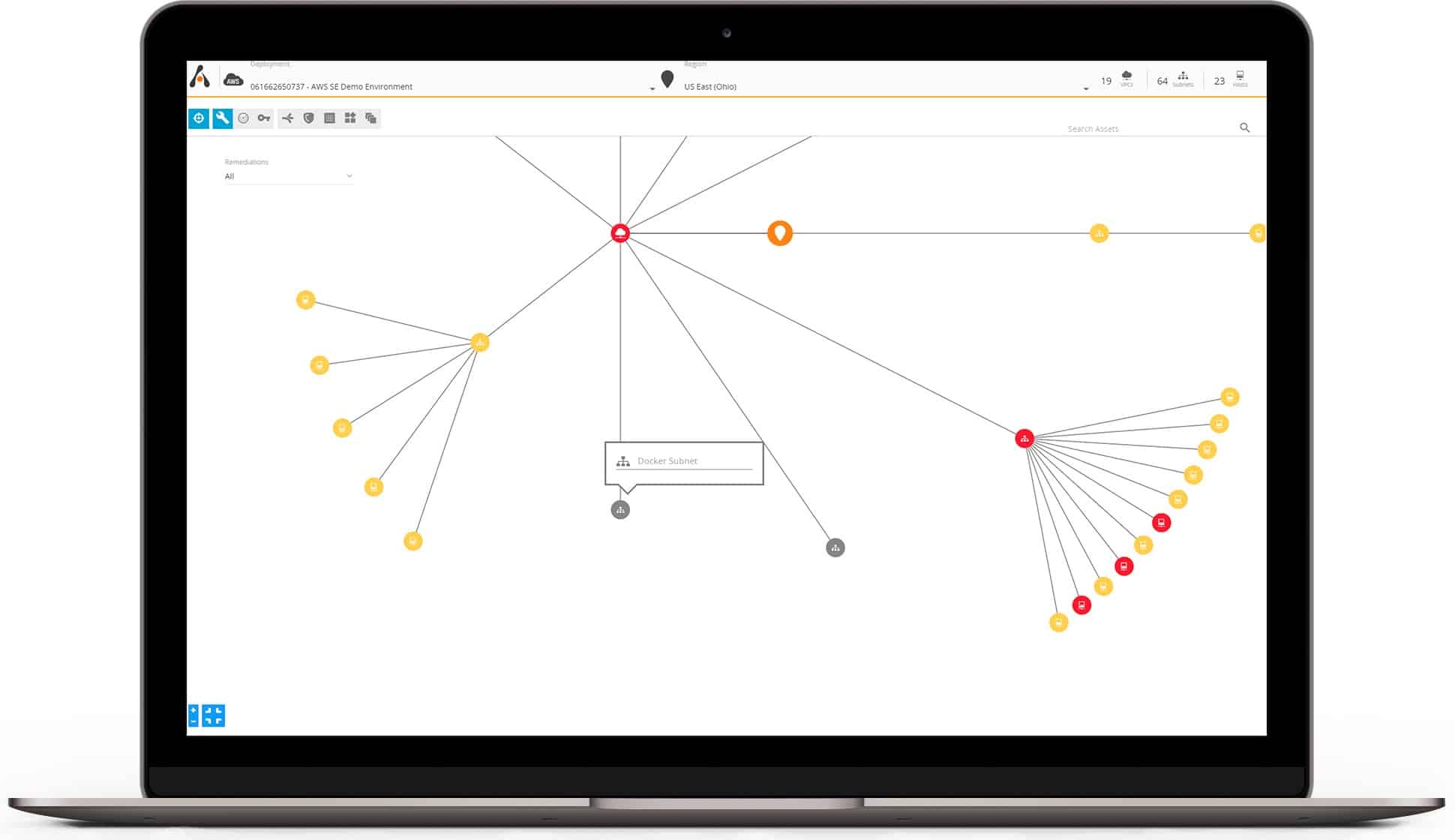
Visualize Your Environment
Using the security overview in the Alert Logic console, you can quickly see your network inventory and relationships in the topology map. With this high-level view, you can assess deployments and prioritize security measures for your corporate IT assets.
- Identify vulnerabilities: Instantly view vulnerabilities and prioritize which to address first, with actionable remediation guidance
- Customizable mapping: Add data from other network asset sources using the Alert Logic Asset API
- Real-time scanning: Configure the network discovery scanner based on your actual environment’s topology
The Benefits of Choosing Alert Logic
Alert Logic delivers a comprehensive solution, providing asset visibility, vulnerability assessments, and threat detection and response for optimal security coverage. This enables broader detection with less effort and reduced cost.
And with Alert Logic, you’ll have a solution for dealing with shadow IT risks. This refers to technology solutions, software, or devices used within an organization without explicit IT department approval. These hidden assets pose significant security risks, as they may bypass standard controls. Alert Logic’s network discovery solution helps uncover shadow IT, ensuring complete visibility into all devices and services operating within your network.
SECURITY PLATFORM
- Network asset discovery
- Extended endpoint protection
- Vulnerability scanning
- Threat monitoring and visibility
- Intrusion detections
- Security analytics
- Log collection and monitoring
THREAT INTELLIGENCE
- Verified testing 2.1 million + web application attacks
- Dark web scanning
- Remediation guidance
- Attack prevention capabilities
- User behavior anomaly detection
- Event insights and analysis
- Threat frequency, severity, and status intelligence
- Comprehensive vulnerability library
EXPERT DEFENDERS
- 24/7 SOC with incident management, escalation, and response support
- PCI scanning and ASV support
- Service health monitoring
- Incident response assistance
- Threat hunting
- Help with tuning strategies, customized policies, and best practices