300%… 300%…
…I’m envisioning the late Johnny Carson with the envelope pressed up to his turbaned head, and answering with some witty commentary on political mishaps, scientific oddities, or economic blunders. But this number represents something much more startling and probably too hidden for late night talk show host writers to stumble upon. What is the 300% I’m referring to?
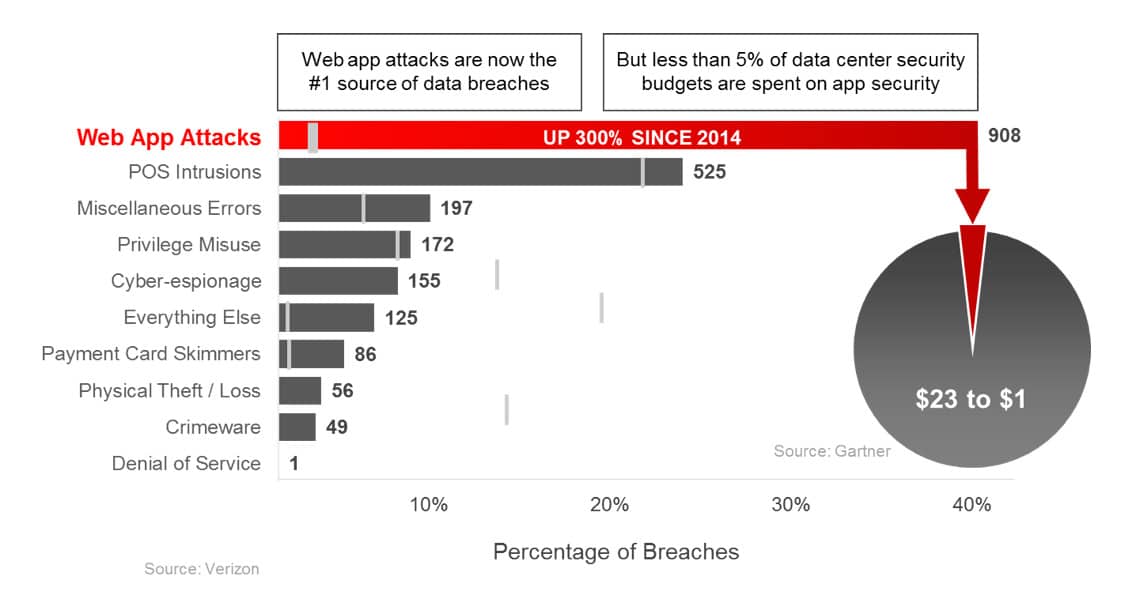
It’s the % increase in data breaches, from 2014 to 2016, that resulted from a web application attack – as reported via the 2016 Verizon DBIR. Let me state that again… a 300% increase in confirmed breaches that were driven by a web application attack. This is by far both the largest single source of attack resulting in successful data breaches, as well as the largest increase in an attack vector in recent cyber security history.
And in parallel, Gartner and Veracode published a survey finding that “less than 5% of IT security budgets are spent on application security”. An inconvenient set of competing factors indeed.
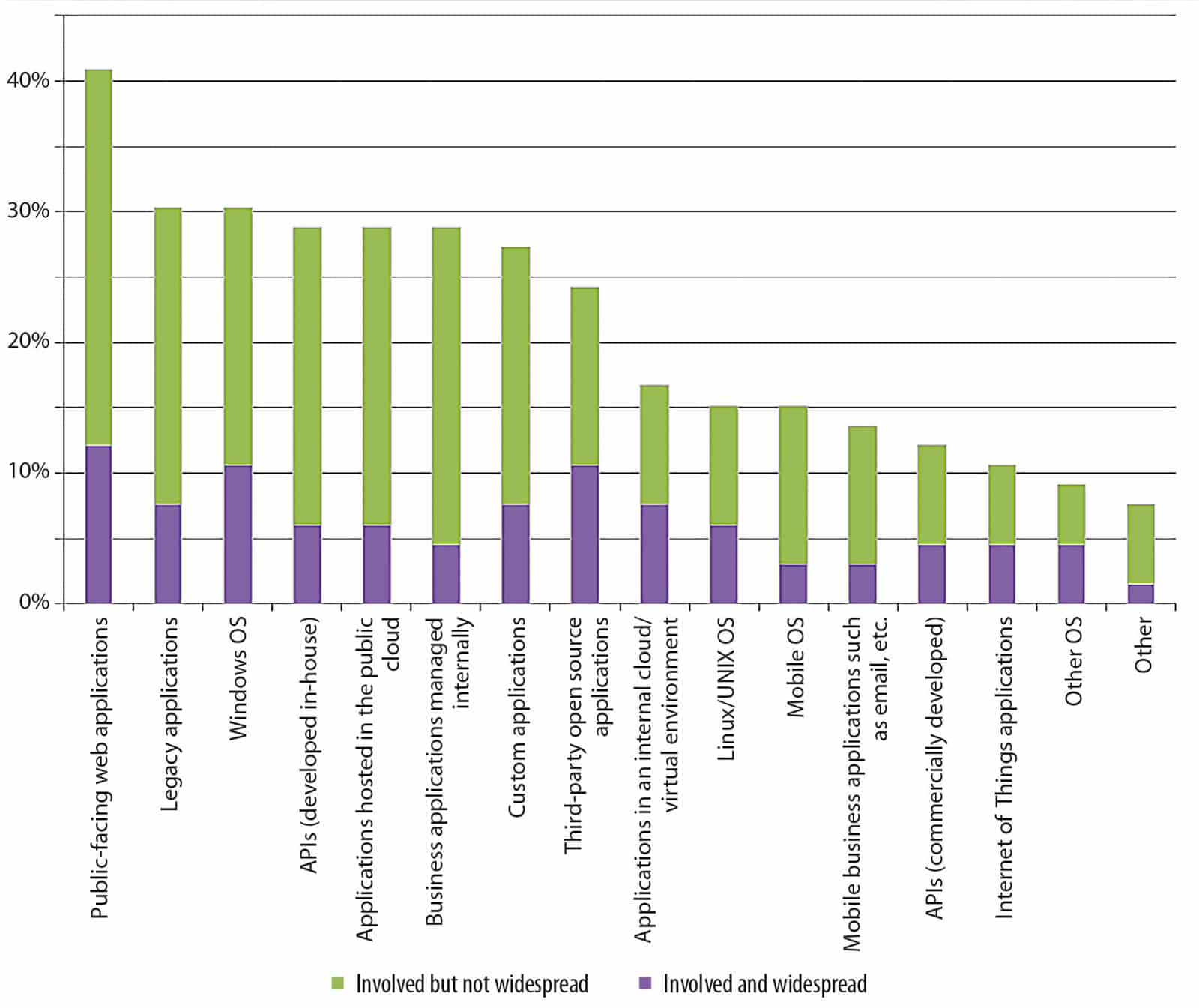
Public facing web applications and cloud-based applications top apps involved in data breaches
Another stat that hit me in the gut a bit was the recent SANS Institute State of Application Security Survey finding around the prevalence of different applications role in security incidents. The 475 respondents admitted that their public facing web applications were the leading application type involved in a data breach. Interestingly to note as well is that teams are also seeing applications hosted in public cloud as a top contributor to data breaches.
Source: SANS Institute
While DoS and malware-driven events hit the news more frequently, web application attacks – going after the valuable soft underbelly of most organizations application portfolios – are crushing the exploit competition – with little expectation of a slowdown.
Now, I’m not a big fan of scare tactics masquerading as marketing messages – a prolific approach used by many security vendors. But, in this case, these statistics are remarkable enough in and of themselves to deserve a discussion – not a fear-laden sermon – but a rational unpacking of the issues and implications that matter.
So, Why Are Web Apps The #1 Source of Breaches?
The basic nature of publicly facing, internet accessible applications is at the heart of the matter – but there is more to it than that. Let’s start with the complexity of the app and infrastructure stack. Applications have become more complex due to requirements for user and system interaction, the insatiable need for innovative capabilities, and usage of open source and 3rd party libraries that string along their own long tail of unpatched vulnerabilities.
With over 7,700 RFC’s outlined for secure coding standards, the idea of building impenetrable web application code is nothing short of a pipe dream. And, many teams are continually developing and deploying application workloads that are no longer ring fenced by traditional firewalls.
The Multiplier Effect on Your Attack Surface
Multiply a single application stack’s complex set of possible vulnerabilities by the number of unique applications being managed within a portfolio, then throw in the variability of multiple hosting environments in today’s hybrid IT environment, and you can imagine the effect this has on the attack surface.
What to do with This Info?
Each businesses application portfolio is as unique as your business, so coming up with a standardized canon of best practices is naïve at best. What we have learned – working with the thousands of Alert Logic customers who are tackling the layers of issues surrounding this reality – is that the first steps always revolve around awareness.
- Be aware of the problem at large and the stay abreast of the preferred attack vectors
- Be aware of how your application portfolio impacts your organization’s attack surface
- Be aware of the shared responsibility model when deploying web application workloads via a public cloud service provider
Easier said in a blog post than done… but alas, awareness is always the first step in any important change. From there, your specific decisions to mitigate the risk to your web applications becomes as particular and interesting as your business.
Continuing The Conversation
I trust this post either solidified some issues that you are already aware of, or introduced some eye opening data points to help widen your aperture to a critical piece of your attack surface. We will continue to unpack this topic over the course of the next month – discussing the vulnerability long tail, disclosing vulnerability and exploit data gathered and analyzed by the Alert Logic Managed Detection and Response team, and discussing ways in which teams can keep reducing their attack surface while still garnering all of the business benefits web applications offer.