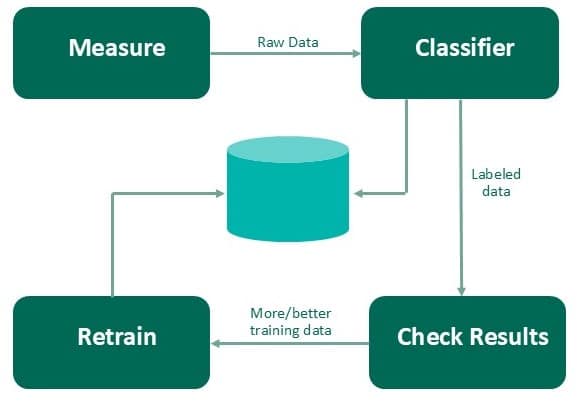
All data has value. Sometimes you just don’t know what that value is yet. The first step is capturing and storing the data, but the challenging part is sifting through it all effectively and efficiently in order to extract relevant or critical insights. An important tool in preventing SQL injection (SQLi) is log data.
Intelligent & Consistent Log Analysis
The various elements of your infrastructure produce logs – access, system – that contain all sorts of data about what is happening in your environment. Your security technologies {like intrusion detection systems (IDS) and web application firewalls (WAF)} also produce data about your environment by capturing traffic and producing logs based on that traffic. Analyzing all that high-value data in an intelligent and consistent fashion can lead to information about successful cyberattacks against your environment.
Pulling all that data into the same central spot (log management tools are a good solution here) so that you have a single pane of glass for the next phase: analysis of all that data. For instance, your intrusion detection system may have had a signature fire on malicious traffic, but the attacked server was not vulnerable to that cyberattack. You can probably conclude that the attack failed in that scenario. However, if the server logs show a successful login and a large amount of traffic going out to the Internet in a relatively close period after the attack, you likely have an issue that needs to be raised to the incident response team.
The cyberattack in the example scenario above seems like is a simple issue to find. However, finding all the pieces to correlate that attack when you have terabytes of data is not simple at all. The mounds of data that can be captured can make it impossible to sort through when only being done by humans. Even small organizations can produce large amounts of traffic data and logs, especially in today’s cloud-enabled world where web applications deploy quickly.
But doing all this log analysis is costly and difficult. Analytics and ML don’t help much if there aren’t people behind the scenes like data scientists and other experts who can make sure everything is working properly. While a large enterprise may be able to staff that kind of effort, most companies don’t have those kinds of resources.
Many organizations choose to outsource the task of managing their big data. But what if your company’s core business is retail? While you might have a vast amount of data on pricing, brands, store locations, marketing, and more, you probably don’t have much data related to cyberattacks from external sources. With such a limited dataset, it becomes challenging to meet the crucial requirement of having quality data to effectively train your system.
Managed security services could be beneficial due to their widespread presence across numerous organizations, which allows them to collect a vast amount of data. However, managed security services solutions typically oversee a variety of cloud security appliances from different brands (such as intrusion detection systems and web application firewalls). This diversity means that data from these devices — despite being related to similar types of cyberattacks —c an vary significantly. Achieving consistency in measurement techniques becomes extremely difficult, if not impossible, when the data itself lacks uniformity.
Stronger Web App Security
Business conducted via the web is expected to keep expanding, especially with the cloud offering faster, more flexible ways to develop web applications and manage data. As a result, cloud security becomes essential to safeguarding those web applications and databases. One of the key defenses against web application attacks, such as SQL injection, is ensuring that your application is securely coded. Training developers to adopt a security-first mindset — particularly to treat all incoming data as untrusted — is a crucial step in preventing cyberattacks.
But the burden of web app security should not rest entirely on the developers. Organizations should invest in detection technologies like web application firewalls and intrusion detection systems. These devices allow the security team to see what kinds of cyberattacks are happening so they can decide on the response based on their IT security policy.
The basic blocking and tackling of cloud security should also be given enough attention. Creating, implementing, and maintaining a strong identity and access management strategy is very important when controlling access to your resources in the cloud. Concepts like least privilege and managing permissions with groups can go a long way in limiting resource access to the right individuals at the right time for the right reasons. Patching your systems is another one of those basic tasks that can get missed or setup inadequately. Making sure you chose the right system for patching your systems depends a lot on your environment. Luckily there are a lot of choices.
The key takeaway is that, while securing your SQL-based apps in the cloud requires ongoing effort, there are a few powerful steps you can take immediately to make a significant impact. Don’t let the complexity overwhelm you. Continue doing business and scaling your growth in the cloud with confidence.