Cybersecurity continues to be a growing priority for organizations of all sizes and across all industries. See how the latest stats and trends are shaping plans, spending, and priorities for 2018.
Things change quickly in the world of cybersecurity. With new threats appearing on a daily basis and attackers continuously evolving their techniques, it can be extremely difficult to keep up. If you seldom feel confident you’re making measurable progress and getting ahead of the game, you’re not alone.
In fact, when asked about the state of their security risk, the majority of IT and security pros responded that last year, things actually took a step backward.
Considering 2017 was the year that brought us the biggest ransomware outbreak in history (WannaCry) and a data breach that exposed the personal information of nearly half the United States’ population (Equifax) it’s perhaps no surprise that organizations report they’re facing more dangers online.
To top it off, the start of 2018 coincided with the stunning disclosure of the Meltdown and Spectre vulnerabilities, which put practically every operating system and device on the planet at risk. Progress has been made on patches for Meltdown and Spectre, but it’s come in fits and starts and the (still incomplete) fixes have been plagued with issues.
While risks and threats continue to pile up, the good news for IT and security pros is the challenges they’re facing aren’t insurmountable. A key part of managing them effectively is staying up-to-date on most current threats, but also stepping back to understand the big-picture trends that are driving them.
To help, here are 10 telling stats that provide context for how cybersecurity is evolving and offer insight into what’s coming next.
Turning the tide in 2018: Know the numbers behind the trends
The majority of successful attacks are now fileless. Source: The Ponemon Institute
Trend #1: Attacks are evolving to incorporate fileless techniques
One of the most significant trends we’ve seen in 2017 and early 2018 is the ongoing shift away from using malicious .EXE files to package and deploy malware. This represents a major change in the way attacks are carried out, and it poses a severe problem for traditional security solutions such as antivirus, which rely heavily on analyzing executable files in order to detect threats.
It’s become common to describe attacks that avoid the use of malicious executables as “fileless,” even though they typically do involve other types of files at one stage of the attack or another. The terminology can be confusing, but what’s clear is that these attacks are very much on the rise, largely for two reasons:
- New attack tools and frameworks continue to lower the barriers to entry, making it easier for criminals to use fileless attack techniques even if they have little-to-no technical expertise.
- Fileless attacks techniques are actively bypassing security solutions much more effectively than traditional, file-based attacks. In short, they’re working.
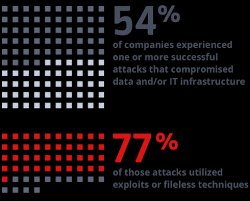
A recent study conducted by the Ponemon Institute found that, when a company was successfully compromised, three out of four times it was by an attack that utilized fileless techniques.
For these reasons, the adoption of fileless attack techniques has been steadily on the rise. While it’s estimated that one in five attacks leveraged fileless techniques in 2016, this year that ratio is expected to be one in three attacks.
The 2017 State of Endpoint Security Risk Report (Ponemon Institute)
These stats make it clear that attacks have evolved, and the majority of currently-available security products are still trying to catch up. That brings us to trend #2.
Trend #2: Antivirus solutions are being replaced or supplemented
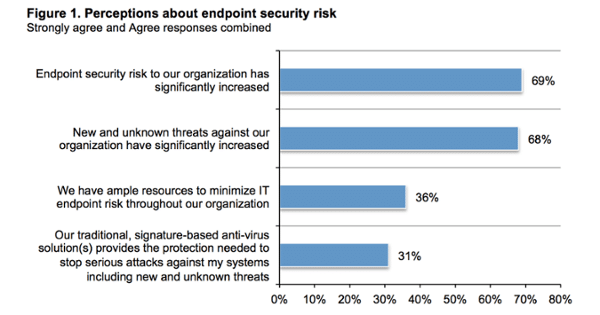
One of the primary reasons why organizations may have indicated their security risk rose significantly in 2017 is that their faith in traditional, bedrock security solutions such as antivirus has been in heavy decline.
When asked whether they agreed traditional, signature-based antivirus solutions provide the necessary protection required to stop current attacks against their systems, nearly seven out of 10 organizations replied “no.”
The 2017 State of Endpoint Security Risk Report (Ponemon Institute)
As a result, the majority of organizations are investigating other options, including next-generation antivirus products and other cybersecurity solutions. Many have made moves to augment their antivirus with an additional layer of advanced protection, while others have invested in alternative solutions in hopes of mitigating damage when attacks do get through. Some are even ripping out their antivirus altogether.
The 2017 State of Endpoint Security Risk Report (Ponemon Institute)
The downside to adding additional layers while maintaining existing solutions, of course, is that it places additional strains on security teams and their budgets. Not only are new tools an additional cost, they’re also another thing that has to be managed on an ongoing basis. That brings us to trend #3.
Trend #3: Security is getting more expensive and difficult to manage
In addition to reporting a significant rise in the new types of attacks they’re seeing, organizations also report struggling to keep the cost and complexity of managing security down.
In an attempt to respond to new threats and provide more advanced protection beyond file analysis, some traditional and next-generation antivirus vendors have begun offering supplemental add-ons and additional features. In many cases, these features require more active hands-on management than teams may be used to, including more intensive whitelisting and far more false positives. In fact, false positives were ranked as the #1 “hidden” cost of endpoint protection in Ponemon’s 2017 State of Endpoint Security Risk report.
Adding to the management challenge is the fact that organizations now have an average of seven different agents installed on endpoints, with each requiring its own monitoring. Simply put—the majority of organizations feel like they’re underwater.
On the plus side for security teams, funding continues to rise, with Gartner forecasting an 8 percent increase in global security spending to the tune of $96 billion, total.
According to Gartner, there are several factors behind the rise, but the biggest motivation stems from the numerous high-profile attacks and data breaches that plagued organizations in 2017. Companies don’t want to become the next Equifax, and they’re increasingly aware of just how costly today’s cyber attacks can be.
Ponemon pegs the average total cost of a single attack at $5 million (or roughly $300 per employee) and indicates the biggest itemized cost is system downtime.
Costs can span a broad range depending on the organization and the scenario, but for the majority of attacks, downtime is indeed the real killer. Having systems locked down or pulled offline can be extremely disruptive, and it can send unexpected ripple effects across an organization’s operations.
Take, for example, the ransomware attack that hit Erie County Medical Center last April. It took the Buffalo, NY area hospital more than three months to fully recover from the incident, with total costs estimated at $10 million.
When attacks hit large corporations, the costs can be even more astronomical. Global shipping giant Maersk reported losses of roughly $300 million from the NotPetya attack in June 2017. The pharmaceutical company Merck acknowledged the attack caused similar losses in Q3 plus an additional $300 million in Q4.
With attacks actively evolving to spread more quickly and cause as much damage as possible, the costs are mushrooming. Cybersecurity Ventures estimated cyber attacks cost businesses $1.5 billion in 2016. Experts estimate the total global losses from last year’s WannaCry outbreak alone were in the ballpark of $4 billion.
These are staggering numbers, and companies have clearly decided additional security spending up front is well worth it if it reduces their risk. The nature of the threats organizations need to be prepared for is rapidly changing, however, and the types of attacks they saw in 2017 are very different from the types of attacks they’re most likely to encounter this year.
Trend #4: Ransomware on steep decline while cryptomining malware booms
It wasn’t long ago that ransomware was the undisputed top payload of choice for attackers looking to make a quick Bitcoin. It dominated the threatscape for a solid two years, during which time it often seemed like it was practically the only type of attack anyone was talking about.
During the first half of 2017, if your company suffered a malware infection it was more likely to be ransomware than anything else. At the peak of the ransomware boom in June 2017, researchers at Malwarebytes reported 7 out of every 10 malware payloads were ransomware.
Then, suddenly, something unexpected happened — ransomware usage plummeted.
In July, the ratio of ransomware dropped to less than 30 percent of all malware payloads. By December, the ratio had fallen below 5 percent.
Ransomware use plummeted in the second half of 2017. Source: Malwarebytes
Experts are pointing to several factors that help explain the dramatic decline:
- Awareness of ransomware reached a tipping point. By the time the WannaCry outbreak hit in May 2017, infecting hundreds of thousands of computers all over the world, ransomware had been steadily growing as a top security concern for years. But WannaCry brought that awareness to another level and underscored just how urgent the threat had become. The mainstream attention it generated fueled renewed interest in learning how infections work, how to handle them effectively, and how to avoid them altogether. If it wasn’t already, for many organizations, addressing ransomware quickly became IT security priority #1.
- Few victims are actually paying ransoms. When WannaCry hit, much of the media attention was focused on how far it was spreading and how quickly. One stat that didn’t garner as much attention, however, was how much money the attackers behind the ransomware were actually pulling in — $143,000. That’s certainly not a bad sum for a single attack, but when you take into account this was the biggest ransomware outbreak of all time, with more than 400,000 computers infected, that paints things in a different perspective. At that scale, it’s a relatively paltry haul (in comparison, Locky ransomware generated over $1 million per month during its heyday in 2016), and it’s extremely telling of ransomware’s biggest problem these days — victims simply aren’t likely to pay.
- Cryptocurrency volatility is tough on the extortion racket. In order to pull off a successful ransomware heist, the stars really have to align for attackers. Not only do they have to infect a victim who doesn’t have reliable backups (or the time/resources required to use them), the victim also has to have quick and easy access to cryptocurrency and be willing to put their trust in a criminal and pay them up front. Making matters more difficult, attackers also have to make reasonable ransom demands, and that means actively keeping track of the price of cryptocurrency, especially during a frenzied boom and bust periods. Otherwise, a particularly good day for cryptocurrency markets can result in some victims being priced out, while a particularly bad day can also dramatically reduce profits.As a cumulative result of all these factors, for many attackers, ransomware has ultimately become more trouble than it’s worth. Especially when there are now easier, sneakier ways of making a buck.
- Cryptocurrency-mining malware provides a stealthier, more effective alternative to ransomware. Why bother trying to extort victims when you can hijack their computers’ CPU power to mine cryptocurrency directly, without them even being aware? That’s the question more and more attackers have been asking themselves lately, and the majority have switched over to dropping cryptomining malware as a result.
Not only does the switch to “cryptominers” take potentially uncooperative victims out of the equation, it also encourages attackers to re-prioritize achieving stealth and persistence for prolonged periods of time. Rather than hitting organizations in the face with ransomware, attackers are going back to distributing malware carefully designed to slip through the cracks. That’s a very big adjustment that fundamentally changes the nature of attacks and how organizations need to defend against them.It’s a shift in strategy that’s already netting attackers millions.
Cryptomining malware has been everywhere in Q1 2018. Here’s a quick recap in case you haven’t been keeping score at home:
- January 5: Python-based PyCryptoMiner botnet infects Linux-based systems
- January 10: Attacker attempts to infect 30% of the world’s networks with “RubyMiner”
- January 11: Attackers make $226,000 installing Monero-mining malware on Oracle WebLogic servers
- January 31: Smominru botnet uses over 500,000 infected computers to generate more than $3 million in Monero
- February 2: New Mac cryptominer distributed via MacUpdate hack
- February 5: “Wormable” cryptomining malware dubbed ADB.Miner targets Android devices
- February 7: Sophisticated data-stealing, cryptomining malware campaign hits U.S. and Asia
- February 12: 4,000 government and other organization websites hacked to mine cryptocurrency
- February 13: Zero-day vulnerability in Telegram messenger app exploited to install cryptomining malware
- February 13: Cryptomining scripts found in 19 Google Play apps
- February 15: Massive cryptomining operation exploits Jenkins servers, makes $3 million mining Monero
- February 20: Hackers infiltrate Tesla, drop cryptominers
And that’s just eight weeks into the year. It also doesn’t cover the activity from 2017, including the WannaMine and Adylkuzz campaigns that utilized the same leaked NSA exploit (EternalBlue) that fueled the WannaCry outbreak.
Malicious cryptomining (or “cryptojacking“) has clearly caught on, and attackers are showing no hesitation adding it to their bag of tricks. In addition to adding cryptomining scripts to malicious or compromised websites, cryptominer payloads have also taken the place of ransomware payloads in a wide variety of malware campaigns. Spam emails and exploit kits are dropping them with increased frequency, and other applications such as Facebook Messenger are being exploited to spread them, as well.
Attackers are also increasingly bundling cryptominers together with other malware payloads such as credential stealers and backdoors, in an attempt to further monetize their attacks (the PZChao campaign is a good recent example).
What the rise in cryptomining malware means for IT security in 2018
The move from ransomware to cryptomining malware represents a significant shift in priorities for attackers. While the former is all about inflicting damage (typically encryption) and initiating a big reveal (ransom screen), the latter is all about laying low, evading detection, and running as quietly as possible in the background for as long as possible.
Organizations that responded to ransomware infections by investing in backup were smart to do so, but now they face a threat designed to infect them just as effectively while silently draining their resources and bogging down their systems over time.
Organizations need to adapt their security efforts accordingly and make sure they’re properly equipped to address infections that aren’t as blatant as ransomware — infections that are instead getting increasingly stealthy and evasive.
How do you fight an infection you may not even know you have? The best answer is preventing it in the first place, and organizations need to prioritize preventative measures like better vulnerability management and threat detection, instead. That will help address the threat of cryptomining malware installed on machines. For malicious browser-based cyptomining, organizations and users can consider installing extensions like No Coin, minerBlock, NoScript, and ScriptSafe.