Many organizations struggle with the same challenges: small security teams, too many alerts to handle, and too few candidates qualified to fill open cybersecurity positions. All of this is elevating the need for automated response solutions, with increased emphasis on response, as industry analysts foresee it being the next battleground for customers in the managed detection and response (MDR) market.
However, fully automated response can bring an entirely new set of problems, some likely worse and with larger implications than where you started. In order to best secure your organization, a response solution needs to have flexibility in automation combined with the appropriate depth and breadth of coverage.
This is where Intelligent Response comes into play.
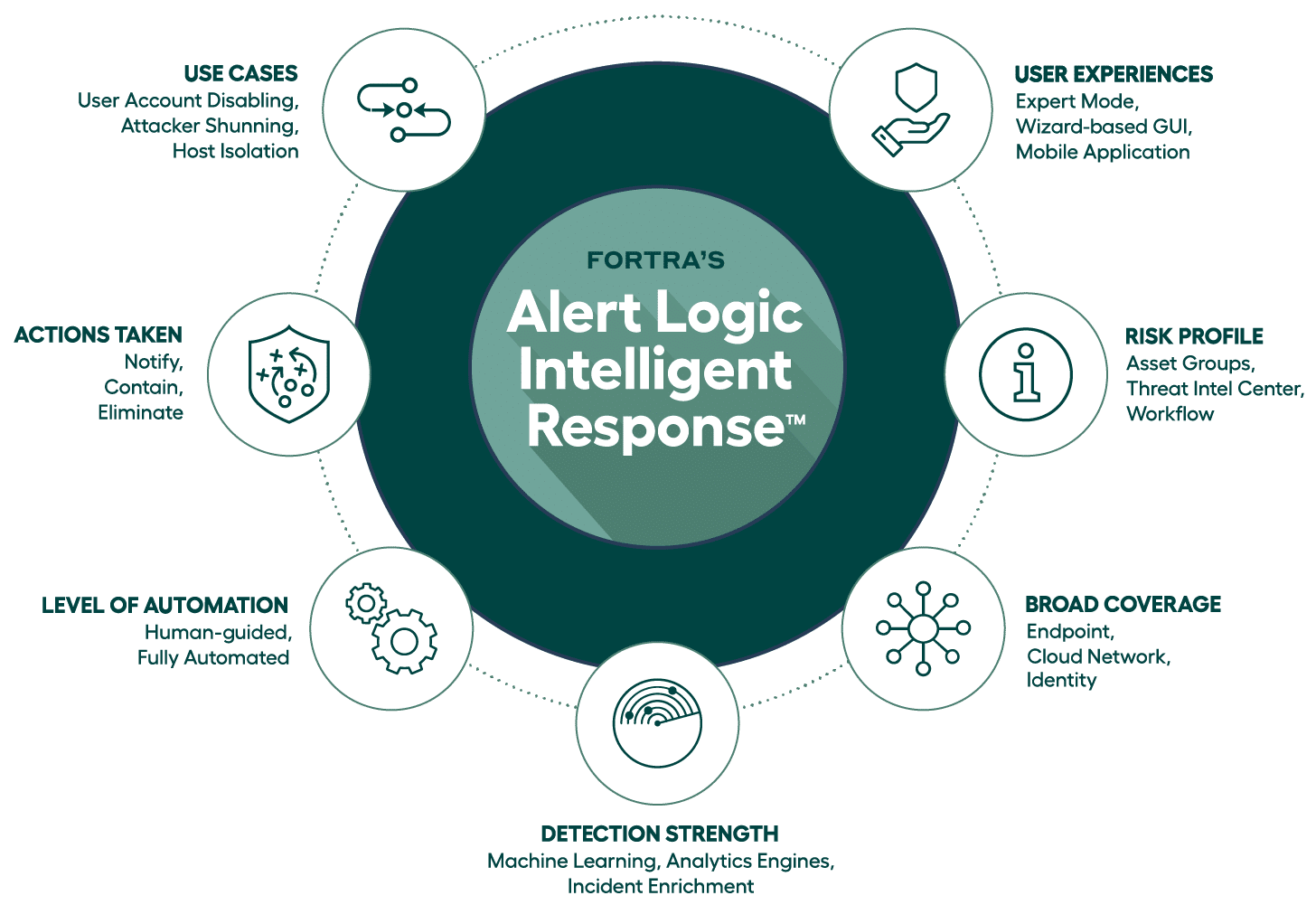
As we considered everything that was needed to deliver an effective response solution, we landed on seven different vectors to help guide our internal development efforts. These vectors naturally addressed the “what” we wanted to get done, but also comprehended “how” it would be consumed and understood there were several underlying technologies and capabilities that needed to be in place to properly execute this strategy.
Fortra’s Alert Logic Intelligent Response
Detection Strength and Broad Coverage
At Alert Logic, our approach to intelligent response begins at the foundation of our managed detection and response (MDR) solution — detection strength.
Strong detection capabilities provide a depth of threat analysis necessary to identify the most effective response. Broad coverage then amplifies breadth, ensuring you’re covered everywhere you operate.
Take endpoint detection and response (EDR) for example. Such solutions offer detection only at the endpoint, which is only part of the answer. After all, if you’re only detecting on the endpoint, you can only respond on the endpoint, leaving a lot of potential blind spots in your environment.
At Alert Logic, we’re able to amplify detection strength and coverage through a broad log ingestion ecosystem, pulling information and telemetry data across your entire environment (endpoint, cloud, network, and identity providers). That data is then analyzed and correlated using machine learning and analytics to enable effective response actions.
Automated Response Use Cases
This kind of analysis informs our global team of security experts, leading to automated response actions that include notifying, containing, and eliminating threats. Through API-based integrations, Alert Logic can notify your organization of incidents and actions via several existing collaboration and messaging platforms, including Slack, Jira, Microsoft Teams, and ServiceNow, as well as by more traditional means like email.
Our solution enables actions to be taken based on customized use cases. When a threat is detected, you can contain the spread by disabling a host, isolating a host, or disabling a user. And you can eliminate threats by shunning an attacker or shutting down a port (which can be done in a human guided or fully automated manner).
With Alert Logic Intelligent Response, use cases and actions are closely linked, which enables you to deploy automation.
Levels of Automation
When deploying new security technologies, most organizations don’t deploy in blocking mode. Rather, they deploy in audit-only mode. This enables them to see what’s going, to gain confidence and become more comfortable before they make the decision to enable blocking.
Our approach to automating response is similar. Most organizations want to see what new policies are going to trigger before automatically letting something happen — and that’s the idea behind human-guided automation.
To simplify human-guided automation, we have developed a mobile application for security analysts. So, when an event triggers, the analyst is immediately notified through the app on their mobile device. The designated analyst can then look at the case and either approve a rapid response or pause for further investigation.
Why would an analyst want this capability? For example, let’s say an organization has a policy stating it’s a U.S.-based company and no one outside of the country should be accessing the system. That means, if ever a login is received from outside the U.S., that login should be blocked, or the user disabled.
But what happens if the CEO, or any other privileged user is abroad and needs access? As the security person, you want to be notified so you can see who the user is and then investigate. These extra couple of steps taken up-front can save a whole lot of user productivity loss and the subsequent executive-induced organizational anxiety.
Another benefit of human-guided automation is in the reduction of false positives. Nothing is going to replace an analyst’s situational awareness of the environment. Exploring false positive alerts takes time, and security analysts are already overwhelmed. However, through human-guided automation, when false positives are identified, you can then fine tune the rules to eliminate future notifications.
This flexibility with Alert Logic Intelligent Response allows you to choose between full automation and human-guided automation, granular to an individual workflow, based on use cases and risk profiles.
Risk Profiling for Consistency and Simplification
Alert Logic Intelligent Response gives you the ability to customize your responses by asset groups using threat intelligence from our Threat Intelligence Center. For instance, you can create different asset groups based on criticality and craft a response strategy that is appropriate and aligns to the risk profile of the asset.
Further, our solution includes out-of-the-box workflow templates. These help simplify automation by providing a pre-built workflow engine you can use to sequence processes and achieve your desired outcomes.
User Experiences
When it comes to security, every organization is unique. Therefore, our solution is flexible and scalable, offering options that accommodate all levels of users and can be right sized to deliver the protection you need. From a fully customizable expert mode for sophisticated security users to an easy-to-use, wizard-based graphical interface for others, our solution provides a user experience that will not only fit your organization today but will unlock more capability as your response maturity increases.
MDR with Intelligent Response
Learn more about intelligent response and the extended SOAR capabilities we have in our managed detection and response (MDR) solution.