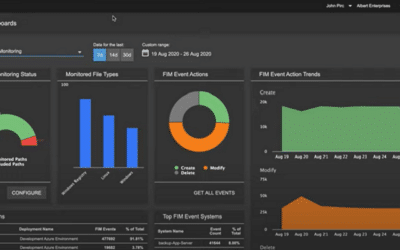
Alert Logic File Integrity Monitoring
A closer look at the value of Alert Logic File Integrity Monitoring (FIM) and how it helps organizations address PCI-DSS (Payment Card Industry Data Security Standard) requirements 10.5.5 and 11.5.
Protect Your Web Apps with Web Log Analytics
Alert Logic Web Log Analytics (WLA) provides the ability to detect anomalous behavior and suspicious activity to protect your web applications and your environment.
Simplify PCI Compliance with File Integrity Monitoring (FIM)
Alert Logic added File Integrity Monitoring (FIM) to help customers achieve and maintain compliance with PCI-DSS (Payment Card Industry Data Security Standard)–specifically requirements 10.5.5 and 11.5.
Extend the Alert Logic MDR Platform with Our DevNet Software Developer Portal
The Alert Logic DevNet software development portal enables customers and partners to extend the managed detection and response (MDR) platform and efficiently extract and work with useful information.
Make It Easier to Manage Workflow with Connectors
Alert Logic developed Connectors to enable customers and partners to automate workflow between the Alert Logic MDR platform and third-party messaging and ticketing systems.
Staying the Course: Delivering on the Promise of MDR
Alert Logic announced ae new features and capabilities for its industry-leading managed detection and response (MDR) platform.
How Security Helps You Win the Race to Digital
The COVID-19 pandemic has accelerated the race to digital for many organizations, but it is crucial to keep security in mind as you embrace cloud transformation.
Cloud Environments Need Cloud-Native Cybersecurity
As organizations embrace digital transformation and adopt hybrid cloud infrastructures, it’s important for their cybersecurity to be cloud-native as well to be effective and scale for the dynamic environment.
Who Are the Stars of a Threat Intel Team?
Threat intelligence is an important part of managed detection and response (MDR), but it is not just one thing. There are many dedicated specialties that make up a winning threat intel team.
Pervasive Ripple20 Vulnerabilities in IoT Devices
An overview of the risks from the Ripple20 vulnerabilities in IoT devices uncovered by researchers at JSOF and how Alert Logic is helping customers detect and avoid potential threats.
Technical Analysis of CVE-2020-12675
A detailed look at the vulnerability in the MapPress plugin for WordPress discovered by Alert Logic security researchers (CVE-2020-12675).
Threat Hunting and MDR
A recap of a Twitter chat between Jack Danahy and Tom Gorup on the role of threat hunting in MDR and whether it should be counted as Tenet #8 of the MDR Manifesto.