Brexit Won’t Get UK Out of GDPR Compliance
Thanks to Brexit, the UK is poised to separate from the European Union. However, compliance with the General Data Protection Regulation (GDPR) will still be necessary even for UK businesses.
Protecting Your SQL-based Cloud Environment — Identity and Access Management
The 4th tip of our 5-part series explores how effective identity access management (IAM) and diligent patching and updating of systems and applications improve your cloud security posture.
Protect Your SQL-based Cloud Environment with WAFs & IDS
We explore the crucial role of web application firewalls (WAF) and intrusion detection systems (IDS) as a layer of defense for protecting web applications in the cloud.
Protect Your SQL-based Cloud Environment — Secure Coding Practices
Secure coding practices are the first line of defense against web application security flaws like injection and cross-site scripting.
Fact Checking the Equifax Data Breach Story
Misha Govshteyn, co-founder of Alert Logic, dives into the Equifax data breach story. He takes a look at what we know and what we don’t know as he fact checks some of the early stories and information circulating.
Buckle Up! Critical Flaw in Apache Struts Puts Web Applications at Risk
A new vulnerability in Apache Struts is putting web applications at risk. Tony Bradley shares more on the flaw and what you should do to protect yourself
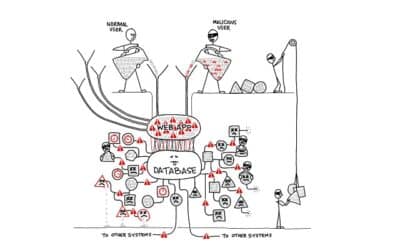
What is SQL Injection, and Why Is It Still Causing Issues?
We dive in for a deeper understanding of SQL injection (SQLi) and why the attack is still one of the most pervasive despite being two decades old.
Tried and True – SQL Injection Still a Leading Method of Cyber Attack
SQL injection (SQLi) remains one of the most pervasive attack vectors despite the fact that it’s also one of the oldest and most widely known.
Are We Saying Public Cloud is More Secure? We Just Might Be
Our 2017 Cloud Security Report shows that hybrid cloud implementations have 141% higher rate of security incidents than pure public cloud environments.
Did you get all that? Recap of Cloud Security announcements at Microsoft Inspire 2017
Read our Microsoft Inspire 2017 Cloud Security highlights. Alert Logic summarizes all the amazing sessions we attended into a concise post.
Emergent PetrWrap Variant Analyzed: Internet Propagation and Recovery of Non-NTFS Victims
We have been digging deeper in the quest to better understand this emergent ransomware strain, PetrWrap and how to recover data for Windows users.
The Curious Case of Alexsey Belan and 1.2 Billion Compromised Accounts
Most of the damage caused by Alexsey is concentrated between 2012 and 2013 connect him to massive breaches at Yahoo, Evernote and Zappos, but we also have some key details behind his techniques.