The ransomware game is ever-changing. As attackers alter their approach, the need for advanced threat intelligence is continuously elevated. Without it, organizations fall short in being able to effectively detect and respond to ransomware attacks.
In this blog, we’ll examine the typical progression of ransomware, how it has changed (and continues to change), and how advanced threat intelligence is necessary in order to be proactive in detecting and responding to such attacks.
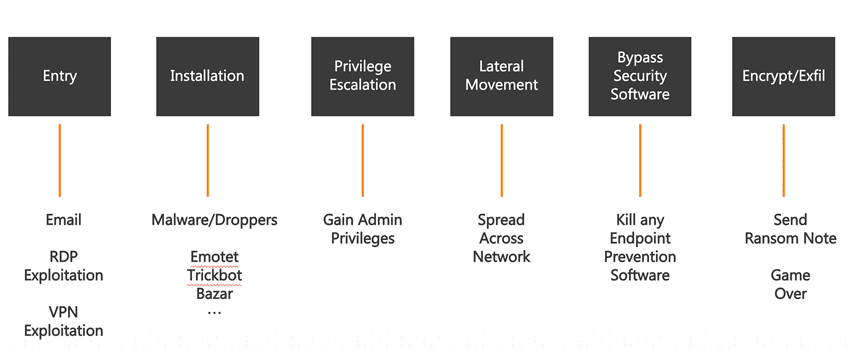
The Ransomware Kill Chain
Ransomware attacks progress along a well-known kill chain. Attackers start by gaining entry to your infrastructure, typically via email phishing or by exploiting virtual private network (VPN) weaknesses or Windows Remote Desktop Protocol (RDP), and then traverse along the chain to install malware, elevate to domain administrator privileges, seek out important hosts, disable security software, and deploy the encryption package.
The process takes time. Anywhere from a few days to several weeks can elapse before the final package is installed and the ransom request is delivered.
But time is not the friend of ransomware creators, and their goal is to shorten the time from entry to encryption from days to hours, as we saw last year with the exploitation of the Windows Zerologon vulnerability.
Shortening the progression, however, is only one of the changes we have seen in the ransomware world.
What else is changing?
Some ransomware creators are shifting their approach. In the past, their goal was to penetrate your infrastructure, propagate throughout your network, and ransom as many machines as possible all at the same time. That approach has been successful, and it is still used. But these creators have learned more lucrative opportunities are available.
In 2020, we saw an increase in some ransomware authors employing a big game hunting strategy, adding extortion to their ransom demands. Before deploying ransomware, these actors will search your environment first, looking for high-value information they think might elicit a bigger payout. If they find something, they exfiltrate the data, and then threaten to sell it on the dark web, advertise the breach, or both.
The key to stopping ransomware is to detect its presence as early in the kill chain as possible and neutralize it before it can carry out its mission.
This is where advanced threat intelligence really makes a difference.
Threat Intelligence Innovation
At Alert Logic, our Threat Intelligence team has a singular focus: to help you detect attacks and attackers in your network. We do that by supplementing our own internally curated systems and data with information available from external sources such as open-source blacklists, Shodan, etc.
Using Threat Intelligence for Proactive Hunting
Alert Logic consumes these disparate data sources along with internal mining of log attack data produced from our analytics engine to formulate threat intelligence that can be used to proactively hunt for attack profiles.
How does this work?
Example: Cobalt Strike
One example is hunting for Cobalt Strike. Cobalt Strike is a licensed penetration testing framework from Strategic Cyber LLC and is a powerful command and control tool. Using leaked source code, ransomware creators often use this tool to elevate privileges and laterally move throughout compromised networks.
Cobalt Strike is typically delivered early in the kill chain as a command-and-control mechanism. Therefore, if the elapsed time of the entire kill chain is two hours and the presence of Cobalt Strike can be detected in ten minutes, you can take action to stop the attack before significant damage can be done.
Alert Logic uses open-source threat data combined with its own analysis to profile the presence of Cobalt Strike. With that profile, Alert Logic can then hunt, searching Windows logs for beacon information that indicates the presence of Cobalt Strike in the environment.
Another example is using combined threat data to identify hits for Ryuk. Ryuk is a known threat and has been listed on watch lists. By piping in disparate sources of data and processing it, Alert Logic has been able to create an analytic that can be used to search across customer environments to identify the presence of the ransomware.
Staying Ahead of the Game
Ransomware is a continuous threat, and the risk of monetary loss for companies that fall victim to an attack is growing. In fact, the average remediation cost for companies that suffered a ransomware attack in 2020 was $1.85 million (over $2 million for U.S. organizations). And the cost of ransomware incidents worldwide is expected to exceed $265 billion by 2031.
Acting proactively has never been more important than it is today. The key to protecting your organization is to stay on top of new threats as they emerge and to take preventive action as soon as possible. By profiling attacker toolsets and tracking their infrastructure, Alert Logic can generate high fidelity watch lists and active analytics that can help detect these attacks before they can carry out their objectives.
Alert Logic’s Threat Intelligence team continuously analyzes threat data, tracking new attack and propagation vectors for malware and ransomware, creating profiles and watch lists, and incorporating unique detection capability into our Managed Detection and Response (MDR) solution. For more information, check out www.alertlogic.com/managed-detection-and-response/