It would be hard to find anyone who isn’t familiar with ransomware as media coverage of high-profile breaches and criminal ransomware gangs has been extensive. But for those working to secure against a successful attack that leads to extortion, the mindset on ransomware may need to change to thinking about it as an objective that, if successful, results in a ransom demand.
In this blog, we focus on how to think about ransomware, dive into an attack sequence which can lead to ransomware, and detecting, disrupting, and containing ransomware with a defense-in-depth strategy.
It’s Not Really an Attack
In speaking to everyone from CISOs to security practitioners, it’s not unusual to hear their priority is to stop ransomware attacks. Ransomware, though, is the end objective of an attack or sequence of attacks – threat actors are working to be in a position of control over an entire network to encrypt your machines, exfiltrate your data, and then extort you for a ransom that will provide you a decryption key and supposedly keep them from releasing your data on the dark web or selling it. These attack sequences take days to months of work before deploying a ransomware payload can even be considered.
With a strong security posture, you can stop the possibility of ransomware before the sequence reaches the action on objectives (extortion) stage.
Understanding Ransomware Attack Sequences
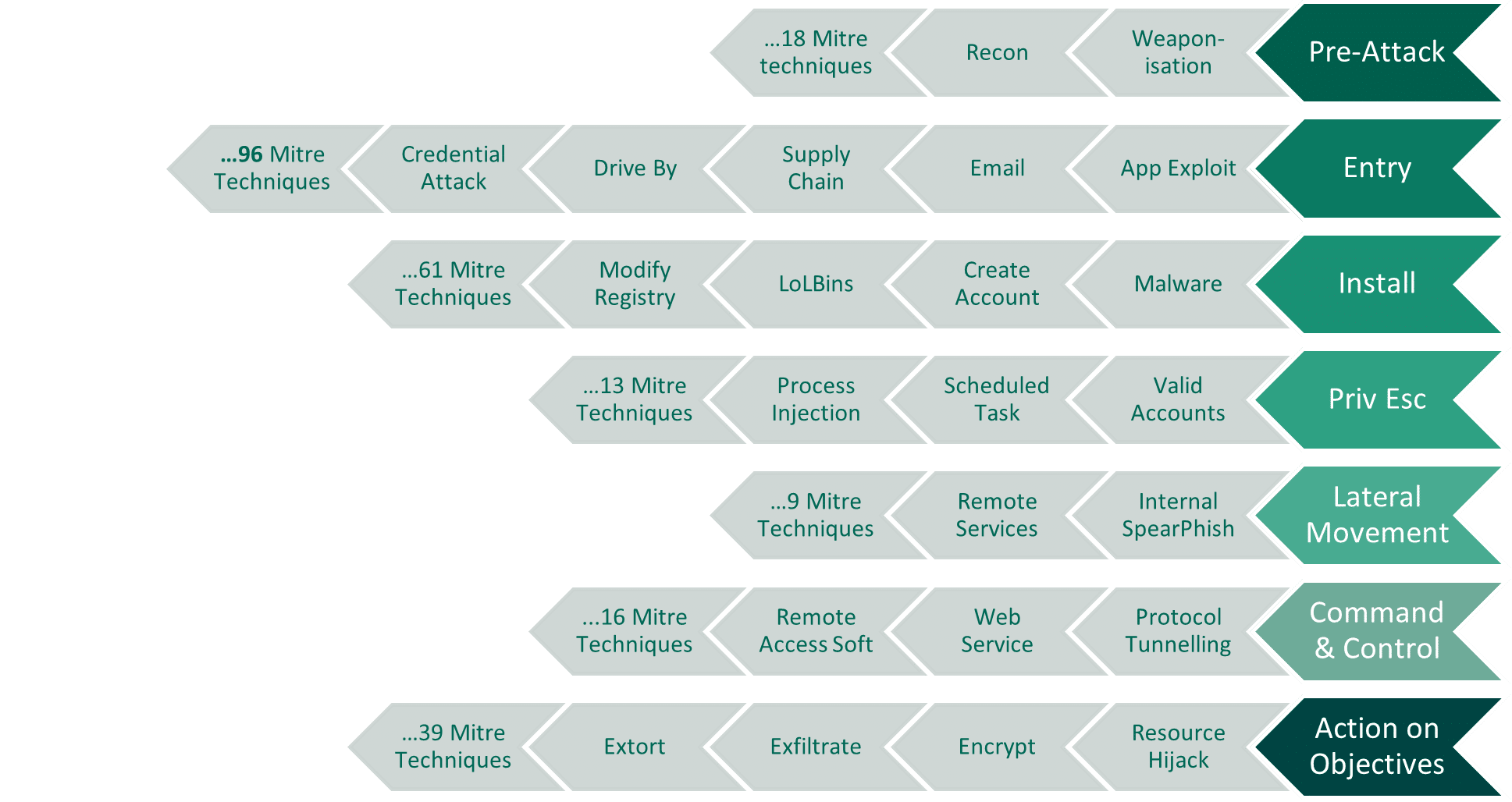
The seven-stage attack sequence shown in the image above is an adaption of the Lockheed Martin Cyber Kill Chain combined with the well-established MITRE ATT&CK framework. A kill chain presents the order in which an attack must progress, while the ATT&CK framework shows the breadth of tactics and techniques a hacker can deploy at each stage. The only piece not represented here is the depth of procedures available to the attacker within each technique — these are continuously growing as the attack surface changes and new procedures, derivatives, or evasions of existing procedures are developed.
Keep in mind that not every ransomware attack sequence is quite this linear; some sequences bounce around in the middle stages as they take control of different devices to have the greatest impact. But for an attack to meet its objective, all the stages must be met.
Seemingly daily, attackers employ new or modified exploits and procedures, and we also see shifts to different techniques. Attackers refresh their methods to try to live in the gray area of unknown and undiscovered attack sequences as it gives them the greatest chance of evading detection and prevention mechanisms and reaching their end objective.
While one of the pillars of a security strategy is to prevent an attack from reaching even the first stage, the reality is there is nothing that blocks 100% of cyberattacks. However, we do not have to stop every attack that grants unauthorized entry in order to stop ransomware. Preparation and the right tools and team in place can identify and head off an attacker before reaching the point of extortion.
Stages of a Ransomware Attack
Let’s take a closer look at each of the stages of a ransomware attack as well as highlighting some of the many techniques an attacker could choose from.
Entry
Entry can be understood as an attacker trying to find a way onto a targeted machine, also known as initial access. Attackers have many options to choose from, such as web exploits which can be sent over the internet to exploit a known or unknown vulnerability to trigger remote code execution. Another common method is a phishing email; if a victim clicks a malicious link, the attacker can begin to take control by stealing credentials or installing themselves onto the compromised machine.
Installation
Installation is focused around using the initial entry to create backdoors and persistence mechanisms. This usually is accomplished by downloading malware or scripts which can cause legitimate programs to run a malicious action. The latter technique is referred to as a living off the land binaries (LOLbin) which is often favored because it can be challenging to separate the malicious outcomes from legitimate administrators using a tool like PowerShell to install new corporate software. It’s not feasible to block such tools; endpoint protection tools, including EDR, need to have a high degree of confidence to take a blocking action or risk overburdening IT teams with false positive blocks.
Privilege escalation
Privilege escalation is important for ransomware, as the attacker usually needs an elevated level of account permissions to achieve their end goals. When attacker gains entry, it is common that they take over a low-level user such as a service network account. Some entry exploits allow for execution of privileged commands to move laterally into the rest of the network; a separate technique may be needed to achieve persistent privilege escalation. An attacker may look for valid accounts with high privileges that they can take over or create illegitimate new ones. Attackers often find success in using an account that has been dormant for a while or where an organization’s digital hygiene is lacking, compromising a highly privileged account that should have been decommissioned. They also may look to deploy credential dumping tools which can grab clear text passwords or password hashes which can be brute forced. With this access, attackers can move laterally through your environment to take control of numerous machines to take complete control of your business so ransomware will have the maximum impact and increase the likelihood of a payout.
Command-and-control
In the command-and-control stage, attackers establish a channel of communication to compromised devices within the target network. In reality, command and control happens throughout an attack sequence, but the technique may vary based on what is available to the attacker. Common examples include using remote access protocols like a remote desktop protocol (RDP), but when forced to get creative, attackers may use social media to blend in with usual internet traffic but also issuing commands through a Twitter/X feed. When command and control is established in enough devices, they’re ready to take action on their objectives, in this case to encrypt, exfiltrate, and extort. The attacker also may look to disable your preventive or insurance controls, such as disabling backups or threat prevention software. Their objective is to cause the most devastation that will lead to a higher ransom.
The Importance of Threat Modeling
Threat modeling is critical to protecting your organization and will help you identify the possible routes to ransomware. As you identify the numerous potential sequences through threat modeling, you can deploy prevention and detection controls creating defense in depth.
As highlighted in the attack sequence, attackers have a whole Swiss Army Knife of tactics, techniques, and procedures they can deploy, allowing them to be agile and pivot if they hit an obstacle when progressing their attack. Therefore, a multi-vector approach to detection and prevention is essential to ensure you have the visibility you need to identify malicious activity and contain it before it reaches ransomware.
Relevant security data sources need to be ingested in the form of logs, network packets, and security tooling telemetry. These need to be analyzed to identify instances requiring further investigation where a security specialist can build up a complete understanding of the attack sequence so you can:
- Determine how far the attack has progressed
- Identify all compromised assets and persistence mechanisms
- Work backwards down the attack sequence to prevent reoccurrence
This is an ongoing process rather than a point-in-time exercise. And while you can’t defend against everything — novel threats, emerging threats, and zero days are harder to defend against as they have yet to be seen — it is incredibly rare that an adversary will have a completely novel attack sequence. Therefore, with a defense-in-depth approach and timely investigations, you will know when an attacker has gained unauthorized access and can intervene before they cause any substantial impact.
Ransomware Security Controls
As you implement security controls to strengthen your defense in depth for disruption of a ransomware attack, the first four elements of the NIST Framework for ransomware are key.
Identify
In this mapping area, the focus is having visibility into your assets and processes to uncover risks that might be present, both in the cloud and on-premises. Make sure your configurations align to tighten your attack surface as much as possible. Focus areas in this phase include:
- Adversary simulation
- Application security testing
- Cloud security posture monitoring (CSPM)
- Data & asset discovery
- Data classification
- Penetration testing
- Red team operations
- Security & risk assessment
- Security configuration management (SCM)
- Vulnerability management
With a detection and response security solution, such as Fortra XDR and Fortra’s Alert Logic MDR, our goal is to unify many of these elements to provide a comprehensive suite that enhances your cybersecurity. Our focal areas in the identify side include asset discovery so we know what your assets are, what instances have been spun up in the cloud, and what containers are running because if you don’t know what assets you have, you can’t protect them. Once all the assets are identified, we move into vulnerability management, identifying what’s going on in each asset and what potential threats there may be. We utilize a combination of host-based scanning, network scanning, and external scanning so we have a 360-degree view on potential threats and exploitations.
Protect
In the protect stage, the goal quite simply is to prevent an attack from succeeding. Even if your IT environment is vulnerable to attack, you can stop it with the right controls in place, which include:
- Anti-phishing
- Authentication
- Collect feeds from prevention technology
- Email security
- Endpoint protection
- Firewall
- Managed web application firewall (WAF)
- Secure email gateway
- Security awareness training
- Threat intelligence
With detection and response solutions, while our focus is detection and response to provide the level of protection needed to stop an attack aiming for ransom, we need access to collect feeds to pull them into our detection strategy. Investigating a block that occurs when an attacker has already gained entry, is crucial for containing the attacker, as a block may only disrupt the attack sequence, allowing them to try a different approach.
Detect
A strong detection strategy quickly identifies recon attempts (pre-attack indicators), successful attacks, and attacks that suggest insider threat access. Threat intelligence is a critical element. The more feeds and data you have access to will lead to more valuable and timely detections that reduce dwell time and limit the impact an attack could have by preventing the sequence from progressing. Elements of your detection plan should include:
- Log management
- Network traffic analysis
- Container IDS
- Emerging threat hunting
- Forensics
- Integrity management
- Security information & event management (SIEM) or extended detection and response platform (XDR)
- 24/7 SOC
- Threat intelligence
Superior detection is at the core of an effective MDR and XDR solution and each element listed here should be included as part of the service. At Alert Logic, our MDR and XDR solutions’ mean time to detect for automated detections from the moment an attack is identified by our analytic engine is about four minutes, which includes qualifying the attack and escalating to our customer to initiate the response process.
Respond
With your response strategy, the goal is to quickly reduce a successful attack’s impact by disrupting and containing attack sequence before actions on objectives are realized. Once contained, you can move on to full remediation of compromised devices.
To be able to respond quickly, you need an effective incident response plan in place that is regularly tested, practiced, and updated as needed. Tactics of this stage can include:
- Automated response
- Shun attacker
- Isolate host
- Disable credentials
- Endpoint detection & response (EDR)
- Forensics
- Incident response planning
- Identity governance
- Phish mitigation
- Remediation actions
With a true MDR and XDR solution, your remediation actions are developed and ready as needed. When an attack occurs, you have automated response playbooks in place to shun an attacker, isolate the host, and disable their credentials. The visibility our solutions offers allows detections to be made outside of a preventive/response technology to be triggered, broadening their reach and effectiveness.
Cybersecurity is an ongoing journey, not a one-time solution you can set and move on from. Whether your protecting cloud, on-premises, or hybrid environment, being prepared for each stage of a ransomware sequence is critical to stop it from progressing and the ransomware objective from being realized. By collaborating with Fortra XDR or Alert Logic MDR, we can work in partnership with you to ensure your IT environment is always being watched and plans are in place to thwart an attack.

