An ounce of prevention is worth a pound of cure — this saying holds especially true for creating a cybersecurity automated response strategy. No organization, regardless of size, can afford to delay planning for both the prevention of and response to cyber threats. The reality is clear: you must either be prepared to act swiftly to minimize the impact of an incident before it happens or work to contain the damage to your systems, data, and reputation afterward.
With a global shortage of skilled IT talent, filling the knowledge gap won’t happen by simply hiring talent. You will need to allow months of training by experts before your team is fully functional. For mid-sized organizations, having your own security operations center (SOC) is expensive and challenging to operate. Threat actors know this, which is why cybersecurity incidents and attacks frequently happen at night, weekends, and holidays, causing damage for days without anyone noticing.
If you are like most organizations, you may also feel unprepared for the inevitable — a devastating breach. Improving your strategic incident response plan and automating security tasks should be your top security objective because speed is of the essence. Having a plan and being prepared for security responses is one of the most cost-effective measures your enterprise can take.
What is Automated Incident Response?
To combat cybersecurity incidents, rapid response is crucial and requires threat detection and response providers to be flexible and agile enough to meet the unique needs and requirements of each organization. An automated incident response program can provide this rapid response and in doing so, free up time and resources of already overburdened IT teams. By utilizing AI and machine learning, automated incident response programs automate low-level, low-risk tasks, such as searching for malware, scanning traffic logs, and triaging security, leaving your human agents free to focus on high-level security issues.
Strategic Approach to Automated Response Maturity
When developing an automated incident response plan, it’s essential to set realistic expectations — this critical initiative won’t happen overnight. The most effective strategy is to prioritize what will have the greatest impact when implemented first. By taking a phased approach, you can quickly achieve meaningful results, focusing on protecting your highest-value assets from the start.
Automating responses should play an important part in your phased plan. However, it’s not a silver bullet nor is it necessary to automate everything. You must first ask what lies underneath that and does it really need to be automated? By targeting the most important elements that require automation and determining your optimal desired outcomes, you better plan for a rapid response to the most critical of assets.
To make it easier, group assets based on risk factors such as:
- Mission critical
- Internet facing
- Testing and development
- Cloud
Once assets are grouped and prioritized from most to least important, implement a phased approach that aligns with your organization’s strategic goals. Maintaining flexibility in your plan will allow for adjustments as priorities and capabilities evolve over time.
3 Phases of Planning
Strategic incident response can take three forms, depending on your needs, staffing, and capabilities:
- Manual
- Fully automated
- Human-guided automation
Many organizations incorrectly believe the goal of effective incident planning is fully automated responses then abandon that objective when they realize the difficulty in achieving it. Yes, your response capabilities should enable a systematic adoption of automation as a vital key to rapid response. However, it’s not an all or nothing endeavor. The best response is most likely a blend of approaches.
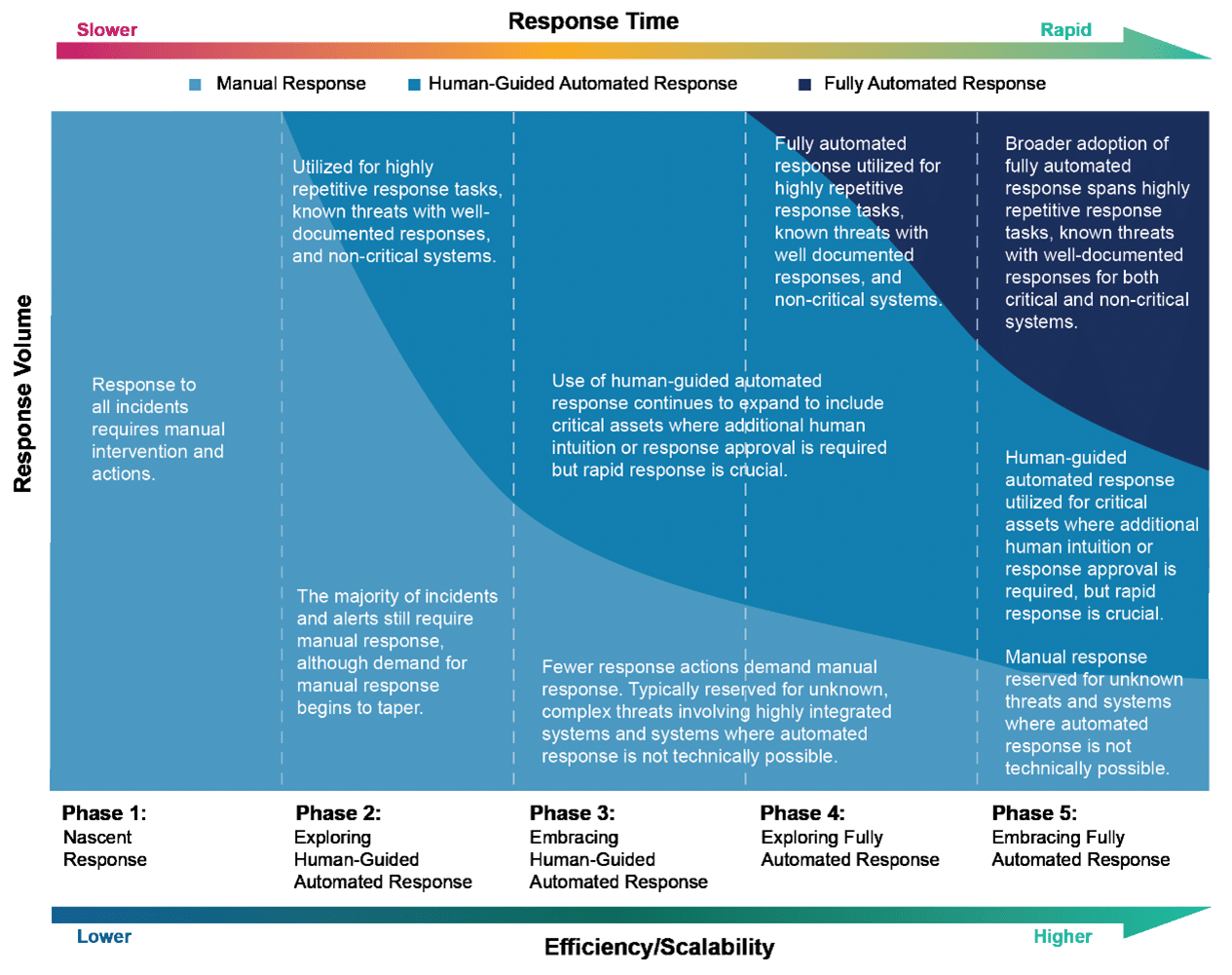
How do you then decide which approach is best for your organization?
Manual response
- Human intervention and action for all incidents
- For unknown or complex threats that require a methodical approach
- Resource intensive and difficult to scale
Fully automated
- No human intervention
- Effective for highly repetitive, time-intensive tasks and non-critical systems with well documented responses
- Provides fastest response
Human-guided automated response
- IT/security staff approve all actions to respond to threats
- Allows IT/security teams to become more comfortable with automation for rapid and efficient response
- Even fully automated incident responses, especially regarding critical assets, can require expertise, intuition, and decision-making abilities only a human possesses
Increased Response Maturity Benefits
The impact and benefits of rapid and efficient strategic response cannot be overstated:
- Free up resources to address other IT and security challenges
- Higher efficiency and scale
- Reduced operational costs
- Lower risks through improved security posture
- Retained customer trust
Although some organizations may consider building their own threat detection, response capabilities, and SOCs , most will find that developing these systems and maintaining 24/7 operations is a resource-intensive, time-consuming, and costly undertaking. Partnering with a managed security services provider like Alert Logic can enable you to quickly realize your identified outcomes and achieve security at scale across an increasingly diverse IT ecosystem with the most robust detection and response solutions in the industry.
