The market is buzzing with the release of Alert Logic Intelligent Response with some asking, How is it different from incident and automated responses?
Understanding Incident Response
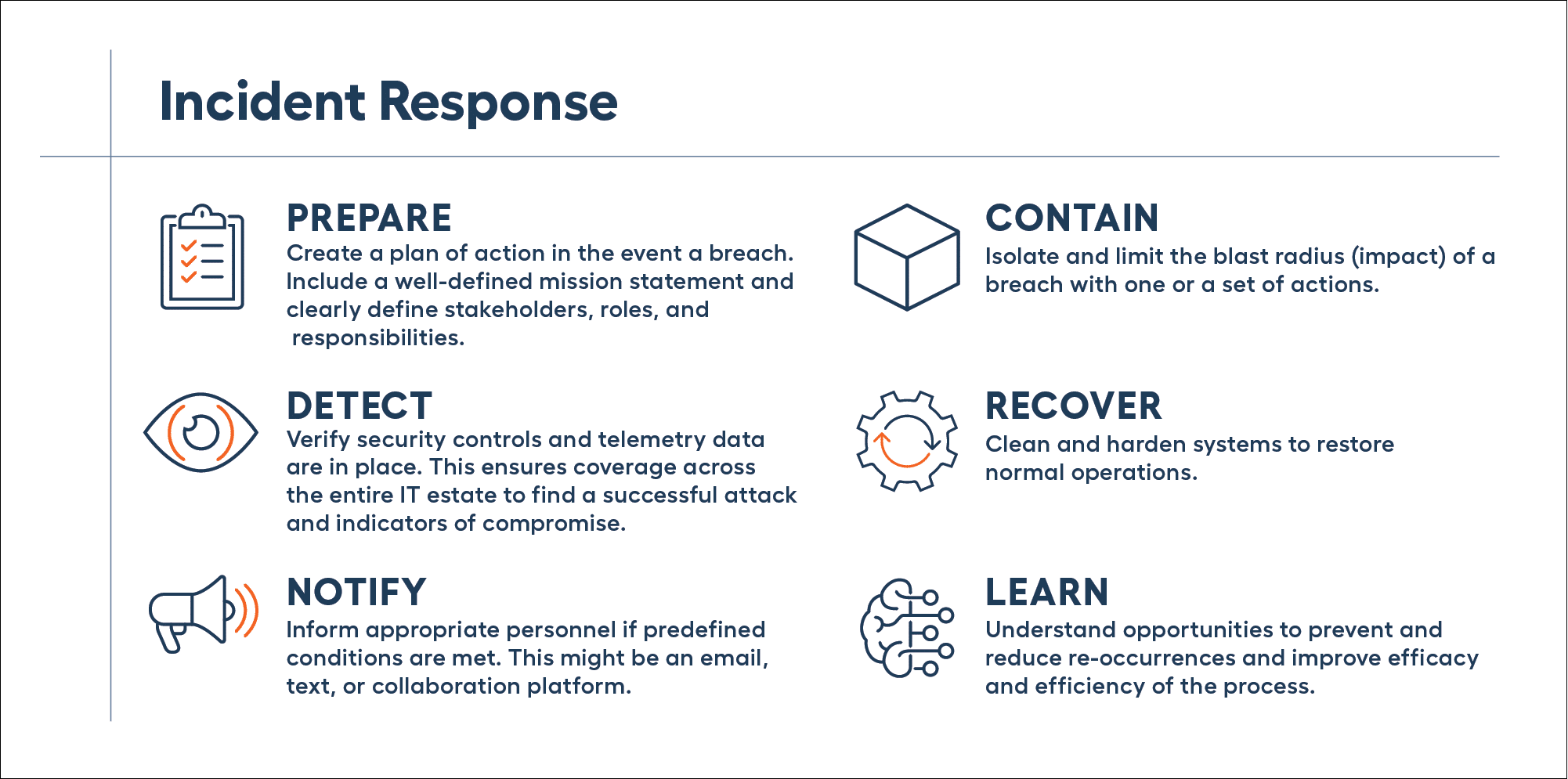
To answer this question, let’s establish a baseline understanding of post-breach activity necessary to minimize the impact of a successful breach. Typically, multiple tasks need to be completed as part of a larger strategy called incident response — the holistic strategy for addressing a breach:
As a best practice, your organization should document your breach process and update it on a recurring basis. The frequency of how often it should be reviewed is unique to each business but take measures to ensure it remains a priority. Too often, organizations dealing with a breach discover their plan of action is grossly outdated with stakeholders no longer with the company. This slows down the process when time is of the essence. At the very least, review and update once a year.
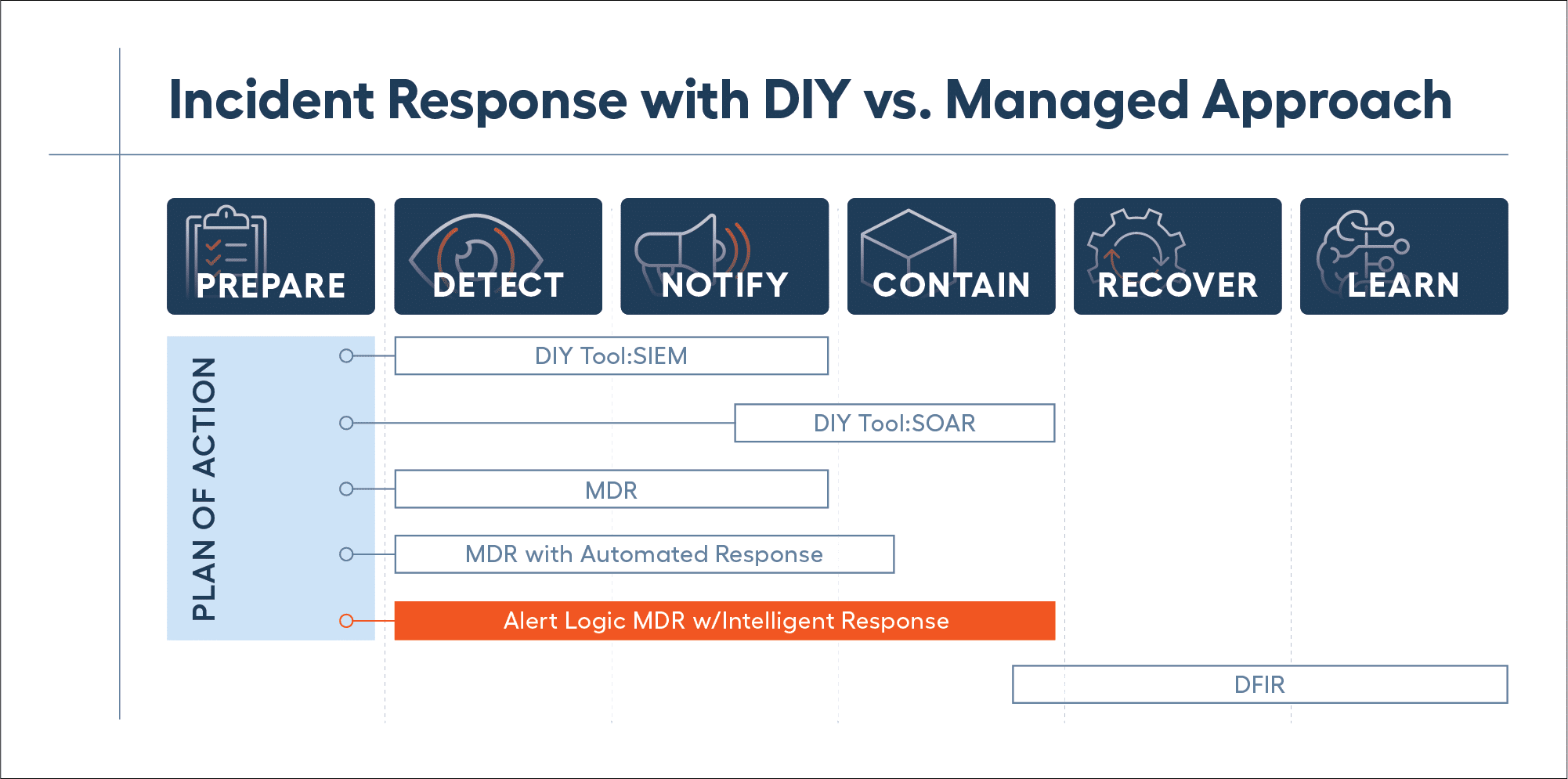
Detection and notification are grouped together and depend on whether the organization prefers a Do-It-Yourself (DIY) or a managed approach. For DIY, a SIEM (Security Information and Event Management) tool is commonly used to ingest telemetry data to detect attacks and indicators of compromise. SIEM is also used to filter out noise and alert appropriate personnel. However, using a SIEM requires dedicated security expertise to deploy and manage it to extract value. Therefore, some organizations choose a Managed Detection and Response (MDR) provider.
Containment is another component that depends on the approach. This is also where response actions start to be automated. For DIY this may be done using a SOAR (security orchestration automation and response) tool. This allows you to create a set of sequenced actions to execute automatically when the right conditions are triggered. Using a SOAR also requires dedicated security expertise and typically requires professional services than can be exponentially larger than the cost of the tool, placing this out of reach for everyone except exceptionally large enterprises with deep pockets. Organizations that choose a managed approach with an MDR provider may have limited automated response capabilities, limited use cases, or incur large professional services fees.
Recovery and learning are grouped together as this is where affected systems return to normal operations. It could include updating the policy on a firewall or cleaning a server with malware. It’s also the time to discover how the breach occurred, the blast radius, and determine if it can be prevented or if the chances of it happening again can be reduced. You may also decide to apply one or more patches or seek third-party assistance from a digital forensics and incident response (DFIR) provider, depending on complexity.
Understanding Automated Response
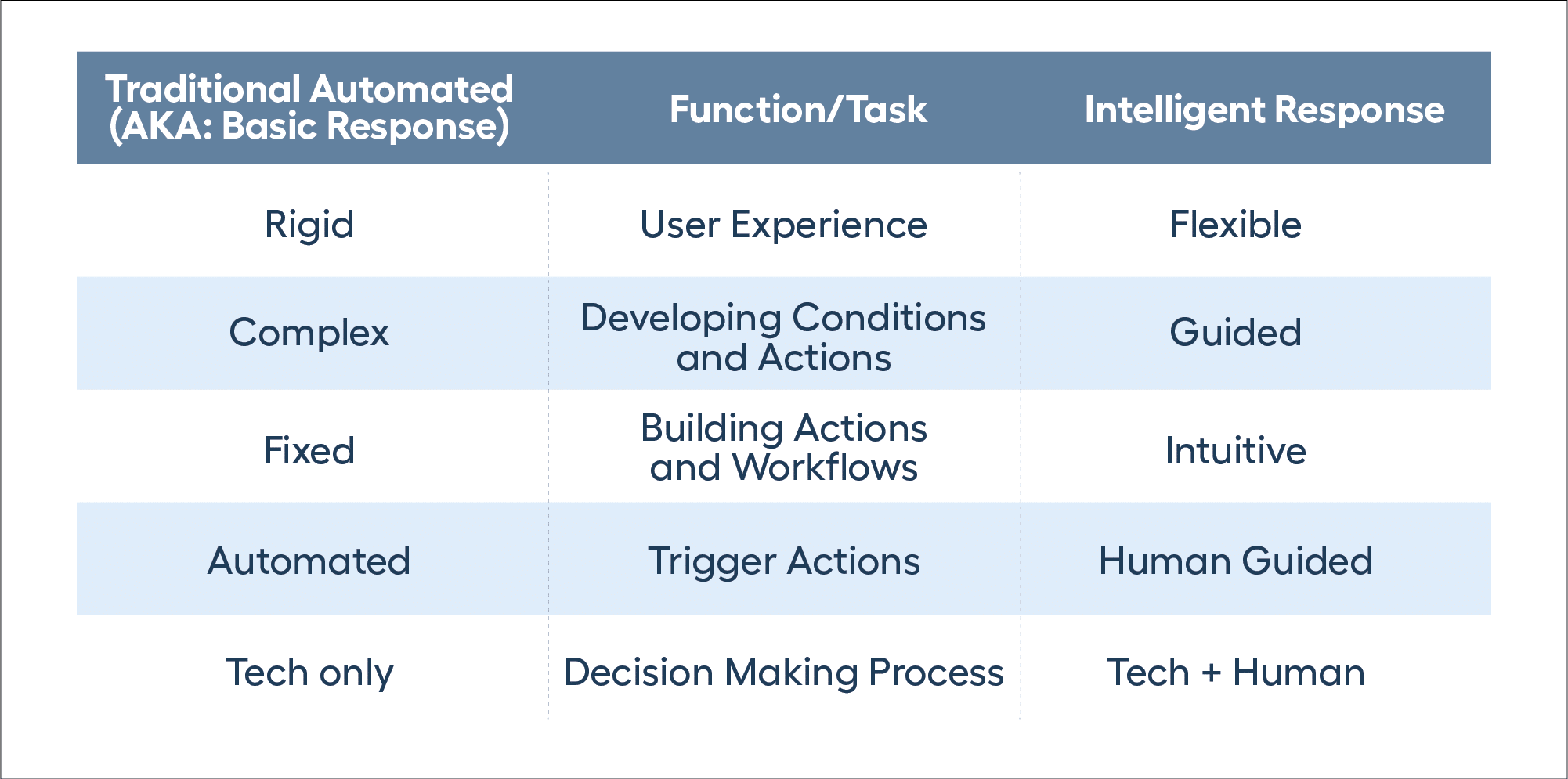
Traditional solutions for automating response are complex and require strong security expertise because they are static. As part of workflows, triggering conditions need to be developed, along with the correct sequence of actions. If the security expertise isn’t available for the organization, then they will spend exponentially more on professional services to deploy and tune for their desired outcome.
Enhanced Automation
Alert Logic Intelligent Response takes automated response to the next level. By leveraging the same security expertise that developed the Alert Logic MDR platform, it provides the right conditions and actions, combined with the right context, for more accurate, human-guided decisions. As part of a holistic response strategy, the solution addresses detection, notification, and containment with multiple actions and use cases in a simplified user experience — making it significantly easier for any organization to create automated response actions.
Alert Logic’s Comprehensive Solution
With bad actors constantly changing their methods to infiltrate and attack sensitive IT environments, there’s no such thing as the completely eliminating risk. To best protect your mission critical systems and sensitive data, assume a breach will occur at some point and have an incident response strategy in place. Simply relying on DIY tools to address the different components of that strategy can come with a high level of complexity and cost, and with mixed results because of their lack of comprehensive protection.
At Alert Logic, we have taken a complex solution and successfully simplified it — Alert Logic Intelligent Response. Now all customers can benefit from the ease and increased protection of automation as part of their incident response strategy to greatly improve their security posture.