As one of the largest, most persistent threats in cybersecurity today, ransomware can be the worst nightmare for companies guarding sensitive data. More and more of our customers are asking about it, eager to stay out of the headlines. This is a reasonable concern. IBM’s Cost of a Data Breach Report 2023 states that the average cost of a ransomware attack at $5.13 million and for the first time ever, ransomware payments surpassed $1 billion in 2023.
But, how does this type of virus do so much damage? What tends to happen when an attack or network breach is in progress? After years of researching and countering ransomware assault, we’ve found plenty of trends and patterns for malicious behavior.
Ransomware Attack Stages
This 7-stage process is the attack strategy we most often see, and it informs our managed security work.
Stage 1 — Targets are Chosen
Bad-faith web actors begin by identifying the best candidates for compromise. Certain industries such as health care, energy, retail, and education are more likely to become a target because they either hold mountains of personal data or have significant financial resources for ransom payments. The hacker might test your IT security protocols to see if there are any weaknesses — for example, a lack of multi-factor authentication or outdated anti-malware/virus defenses.
Stage 2 — An Infection Vector is Chosen
An attacker can use numerous tactics to infiltrate your system. Phishing is by far the most common. The Anti-Phishing Working Group (APWG) observed almost 1.3 million of these assaults in the third quarter of 2022. Phishing usually involves sending employees emails or links that look trustworthy but direct users to a dangerous website or download. Another popular attack vector is leaping over a Remote Desktop Protocol (RDP) with stolen user credentials.
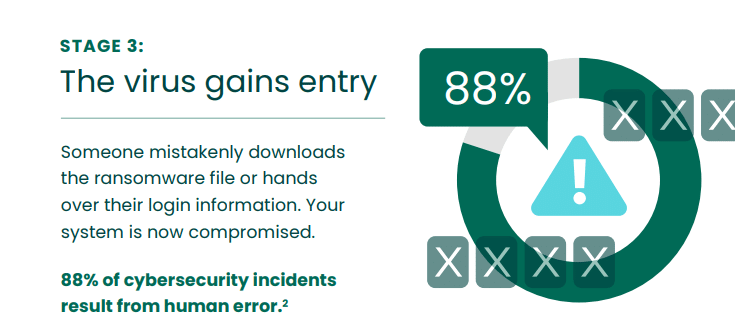
Stage 3 — The Virus Gains Entry
The user is rerouted to a toxic web address, asked to download an attachment, or passes their login details over to someone who appears to be from a legitimate source (e.g., a threat actor impersonating one of their colleagues). The ransomware code now has the single entry point it needs.
[Recommended Reading: What Is Ransomware? How To Protect Your Business]
Stage 4 — Infiltration Spreads
The virus lingers quietly in your system for days, weeks, or months, creating backdoor accounts and escalating access privileges for more attackers. It often moves laterally through connected networks, affecting third-party vendors and other entities linked to the server.
Stage 5 — The Attack Launches
Once the malicious web actor finds a significant number of files, it starts stealing and replacing them with encrypted substitutes. Sophisticated attacks perform this stage automatically by generating a public key and a private key that sits with the web agent, so you can’t access your data.
[Recommended Reading: Changing Your Mindset on Ransomware]
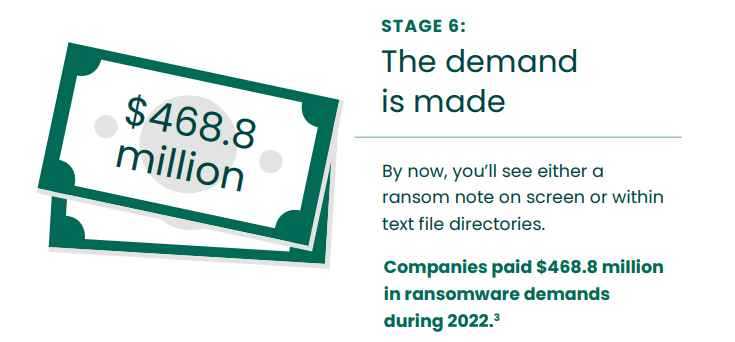
Stage 6 — The Demand is Made
Once the attack is in motion, you’ll likely see a ransom note on your computer screen or in text file directories. The ransom may demand payment in cryptocurrency: useful for anonymous, easy online payments with a payment deadline. The attacker will claim they’ll make your data irretrievable forever if you don’t meet their demands by a set date. One report suggests global ransomware payments were worth $456.8 million in 2022.
Stage 7 — You Deal with the Fallout
With a 24/7 managed detection and security (MDR) provider, you have a much better chance of stopping ransomware from infiltrating your organization in the first place or rooting out an attack before it becomes serious. Data backups and decryption tools are other useful defenses to mitigate any damage. Remember, a successful ransomware assault can leave a larger mark than the initial demand. 31% of U.S. companies end up closing down after they’ve been breached as a result of suffering significant reputational harm.
Ransomware is (justifiably) a hot topic in cybersecurity. And a MDR solution can tip the scales in your favor for finding and dealing with any potential network intrusions. Fortra’s Alert Logic provides human-led threat intelligence to continuously guard your digital assets with immediate incident triaging as needed. Find out more about our ability to protect you from ransomware — get in touch with an Alert Logic expert.