Find out what the latest phishing statistics can tell you about the types of threats landing in your employees’ inboxes in 2018, and how much successful attempts are costing victims.
Phishing continues to be a major concern, not only because the rate of incidents is increasing, but also because attack methods are becoming more sophisticated. The latest stats show the extent of the threat and which tactics are most popular with attackers.
Inboxes are still constantly under attack
76 percent of organizations say they experienced phishing attacks in 2017
No one is safe from phishing attacks. Big and small organizations across all industries are routinely affected. In fact, almost half (48 percent) the respondents to Wombat’s 2018 State of the Phish survey say that the rate of phishing attacks is increasing.
Part of the reason phishing is so popular with cyber criminals is that it provides them with direct access to the most vulnerable part of any network — the end users. Attackers aren’t just wasting the opportunity to get in front of employees with typical spam messages, either. They have replaced easy-to-spot tactics with much more sophisticated techniques that even careful users may not catch until it’s too late.
Case in point: attackers behind Emotet, Ursnif, and other popular banking trojans are increasingly launching campaigns from their victims’ hijacked email accounts. They send their malicious messages to the victim’s contacts, sometimes even replying to existing email chains in order to trick the contacts into thinking it’s a message from the person they know and trust.
On average, 53 percent of IT and security professionals who responded to the Wombat survey reported their organizations have experienced more advanced, targeted phishing attacks (spear phishing) in 2017.
By the end of 2017, the average user was receiving 16 malicious emails per month
According to Symantec’s 2018 Internet Security Threat Report (ISTR), a whopping 54.6 percent of all email is spam. Even more to the point, their data shows that the average user receives 16 malicious spam emails per month, which leads to some scary math. Even if you only have 20 employees, that’s 320 times a month you have to trust in their ability to correctly scrutinize emails and make the right call. That’s 3,840 bullets to dodge over the course of a year.
The increase in phishing means employee training should be a priority, but unfortunately, training videos and mock phishing attacks also only go so far. You can’t rely on every employee to make the right choice every time a malicious email hits their inbox. No one is perfect, and attacks can be extremely well disguised. Eventually, someone somewhere is going to slip up. When they do, you need to ensure you have the right security solutions that can act as safety nets, and you need to have the proper policies in place.
For example, employees need to be encouraged to report phishing attempts without fear of punishment if they were successful, and they need to be provided with clear instructions on exactly how to do so. If your organization is like most, there’s vast room for improvement on this front—according to Verizon’s 2018 Data Breach Investigations Report, users only reported 17 percent of phishing campaigns.
Email is still the #1 delivery vehicle for malware
92.4 percent of malware is delivered via email
Thanks to the accessibility that email provides it’s no surprise it continues to be criminals’ go-to method for distributing malware. That doesn’t mean things are completely static on the malspam front, though.
One of the biggest changes has been a shift away from using malicious attachments to a preference for utilizing malicious URLs, instead. In 2017, for example, Proofpoint reported 3 out of 4 malspam emails delivered malware via attachments. Fast-forward to Q1 2018 and the firm’s data showed that emails with malicious links outnumbered emails with malicious attachments 4 to 1.
The type of malware that spam campaigns are distributing is also changing. For instance, Proofpoint’s Q1 2018 Quarterly Report also notes that banking trojans have supplanted ransomware as the #1 type of malware delivered via email, accounting for nearly 59 percent of all email payloads. Within the banking trojan category, Emotet is the go-to malware, responsible for 57 percent of all banking trojan activity in the first three months of the year.
Most popular malware disguises and phishing lures
Fake invoices are the #1 disguise for distributing malware
Spam and phishing emails come packaged up in all sorts of disguises. According to Symantec’s 2018 Internet Security Threat Report, these are the most common when it comes to distributing malware.
Most common disguises:
- Bill / invoice (15.9 percent)
- Email delivery failure (15.3 percent)
- Legal / law enforcement (13.2 percent)
- Scanned document (11.5 percent)
- Package delivery (3.9 percent)
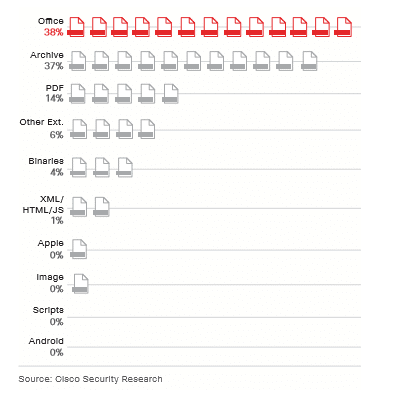
Below are the most common types of attachments attackers use in spam campaigns, according to Cisco’s 2018 Annual Cybersecurity Report.
The most common malicious attachment types:
Top malicious email attachment types. Source: Cisco 2018 Annual Cybersecurity Report
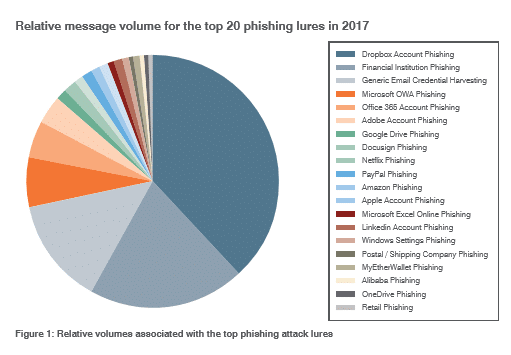
Dropbox phishing lures are the most common; DocuSign lures are the most effective
According to Proofpoint, in 2017, phishing lures associated with Dropbox file-sharing far outnumbered any other lure, accounting for a disproportionately high volume of phishing activity (more than a third of all tracked lures). The next most prevalent lures were those related to financial institutions and generic email credential harvesting.
Most popular phishing lure by volume in 2017. Source: Proofpoint’s The Human Factor 2018 Report
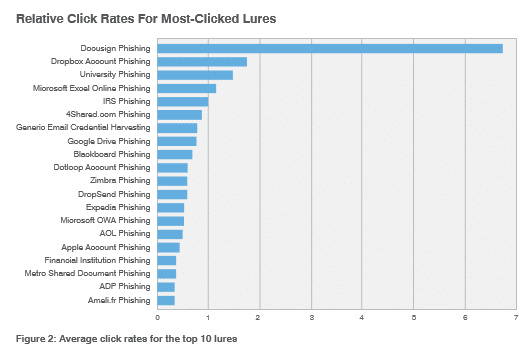
Interestingly, although there were far more Dropbox lures in play, it was DocuSign lures that garnered the highest relative click rate (nearly 7 percent). DocuSign lures were approximately 3x more effective than Dropbox lures. In fact, DocuSign click rates beat out all other credential phishing email lures by a long shot.
Most effective phishing lures on average, by click rate in 2017. Source: Proofpoint’s The Human Factor 2018 Report
BEC scams are growing by leaps and bounds
Business email compromise (BEC) scams cost organizations $676 million in 2017
Though business email compromise (BEC) scams don’t typically garner as many headlines as malware outbreaks and other cyber attacks, they are a serious threat with the ability to cost companies millions.
Unlike other kinds of malicious email campaigns which tend to cast a wide-but-generic net, BEC attacks feature highly sophisticated targeting along with a mix of potential tactics (including social engineering, email spoofing, or computer intrusion) to fool the target into believing that an email is coming from an executive within the organization or from a trusted partner.
Often, the primary purpose of BEC attacks (and the consumer version — email Account Compromise or EAC) is to manipulate the target into executing an unauthorized transfer of funds. According to the FBI’s 2017 Internet Crime Report, in 2017 the Internet Crime Complaint Center (IC3) received 15,690 BEC/EAC complaints with adjusted losses of more than $675 million. This figure is nearly twice the 2016 figure of $360 million.
To bring those figures closer to home, an analyst for Firebird Analytical Solutions & Technologies estimates that the average successful BEC attack earns the cyber criminal $130,000.
Protecting against phishing attacks is an all-hands-on-deck situation
When it comes to protecting your organization from phishing scams, training your employees to recognize bogus emails is a great place to start, but based on the increasing sophistication of targeted attacks, it’s not enough. That’s why Alert Logic offers comprehensive Threat Management to protect companies from malware even when users make a mistake.