One day, the WAF product manager comes to me and asks, “Can we do DDoS protection?”
“Sure,” I said. “We can rate-limit, we have reputational lists, we can auto scale.”
“A big DDoS attack. Think 2 million infected toasters.”
“2 million?” I said, scratching my head. “They would be dumb, but generate a ton of requests, from 2 million different source IPs.”
“Exactly,” he said.
That became the scenario around which we built the on-demand DDoS protection for the Fortra Managed WAF.
Distributed Denial of Service vs. Denial of Service
The terms Distributed Denial of Service (DDoS) and Denial of Service (DoS) often are used interchangeably. While both involve attackers attempting to shut down your website by inundating it with excessive requests or targeted requests that cause heavy workloads on the web servers, a Denial-of-Service attack is significantly easier to stop than a Distributed Denial of Service (attack).
Denial of Service attacks originate from a limited number of source IPs (say, a handful or a couple dozen). For DoS attacks, the attacker typically has close control of the devices used for the attack. These devices are typically servers or computers capable of executing complex code and have good enough network connections to generate an overwhelming amount of traffic to the same target. Some employ amplification techniques to turn a small amount of attack traffic into massive workloads for their targets.
As bad as that sounds, DoS attacks are easy to mitigate. A WAF or even a server can rate-limit or blacklist the small number of source IPs after identifying the large amount of traffic from a single source.
Distributed Denial of Service attacks originate from many source IPs (sometimes in the millions). For DDoS attacks, the attacker builds a bot farm by infecting thousands or millions of vulnerable devices on the internet. Often, hackers rent out their bot farms for DDoS attacks against specific targets. These bots could be laptops and servers, or appliances like toasters and light switches. These devices typically have a more limited ability to execute complex code or generate significant traffic, but there are many of them. Many of the same amplification techniques that work for DoS also work for DDoS.
Unlike DoS, DDoS attacks are notoriously difficult to stop. A well-crafted bot can generate legitimate traffic that looks like a regular user or client. There’s no simple way to distinguish legitimate traffic from attack traffic. On top of that, the attacks would be coming from thousands, if not millions, of source IPs.
Why DDoS?
Why would someone go to the effort and expense to orchestrate a DDoS attack? Why bother slowing down or shutting down someone’s website? There are a number of reasons:
- Ransom: The attacker may seek a ransom or monetary reward to stop the attack.
- Diversion: The attacker may try to overwhelm a security device, such as a firewall or WAF, to hack into another resource.
- Revenge: A disgruntled party (such as an angry customer or former employee) may seek to inflict harm on its target.
- Political: At the state level (political parties or countries), one group may want to shut down access to the opposition’s website to limit access to information, embarrass them, or simply to do harm.
- Competition: One business may seek to limit access to their competitor’s website, especially if doing so drives additional business to the attacker’s website.
- Ideology: Individuals or groups may want to lash out at websites that represent an opposing ideology, such as an environmental group versus an oil company.
- Fun: Finally, there are always individuals out there who do things for fun, to give them a sense of power, or prove their prowess among friends.
Costs of DDoS Attacks
What are the financial impacts of a DDoS attack? Cost estimates for a DDoS attack vary, from thousands of dollars per minute to $100,000 per incident. However, each business and each website are unique:
- How much business would be lost, particularly if it is shut down during the busiest time of the day?
- During the attack, is the business lost for good, or simply delayed?
- How much staff time would be required to stop the attack?
- What are the infrastructure costs (particularly in the cloud) for scaling up to handle the attack?
- Will customers return to the website after the attack?
Traditional DDoS Defenses

Attackers seek to amplify their attack traffic, using techniques that leverage a small amount of traffic to either create more traffic or cause an excessive workload on the target servers. Defenders also seek asymmetrical techniques to make it difficult for attacks to overwhelm their defenses. By making it costly to conduct a DDoS attack, a defender can make it cost-prohibitive for an attack to continue.
There are a number of traditional ways organizations employ to protect against DDoS attacks:
CDNs/Scrubbing centers
The most common defense is to pass traffic through a CDN or their scrubbing center service. Theoretically, they detect and mitigate DDoS attacks if they occur and send you only the clean traffic. However, you pay for these services whether you are being attacked or not. Plus, they tend to introduce false positives or enforce additional verifications when there is no DDoS attack (such as CAPTCHAs or challenges) that unnecessarily inconvenience legitimate users.
WAF
WAFs are great at detecting attacks. They can mitigate DoS attacks by detecting DoS attempts and effectively blocking the source IPs of attackers. But how does a WAF handle many source IPs (thousands or millions)? The best they can do is scale out by adding more WAF resources.
CAPTCHA or challenges (web-server based)
These techniques are effective at stopping attacks on websites where live users access the content. However, these techniques would not work for API websites. Also, if the DDoS attack has enough bots, they can overwhelm the limited resources on a pool of web servers.
Fortra Managed WAF’s On-demand DDoS Protection
Fortra Managed WAF offers a unique architecture that combines the best features of an in-network WAF with the scalable DDoS protection of a cloud environment, all with professional management at no additional licensing cost.
What makes the Fortra Managed WAF’s DDoS protection different?
- We recognize that no matter how much WAF hardware you throw at an attacker, the attackers can always find more toasters to come back at you. Scaling out WAF hardware isn’t the answer.
- We don’t think our customers should pay for DDoS protection when they are not under DDoS attack. Users shouldn’t have to deal with CAPTCHAs or challenges during normal operating conditions. DDoS defenses only should be activated when the website is under attack.
- Cloud providers (such as AWS and Azure) can absorb even the largest DDoS attacks.
- Asymmetrical techniques are employed to make it expensive for DDoS attackers to achieve an effect.
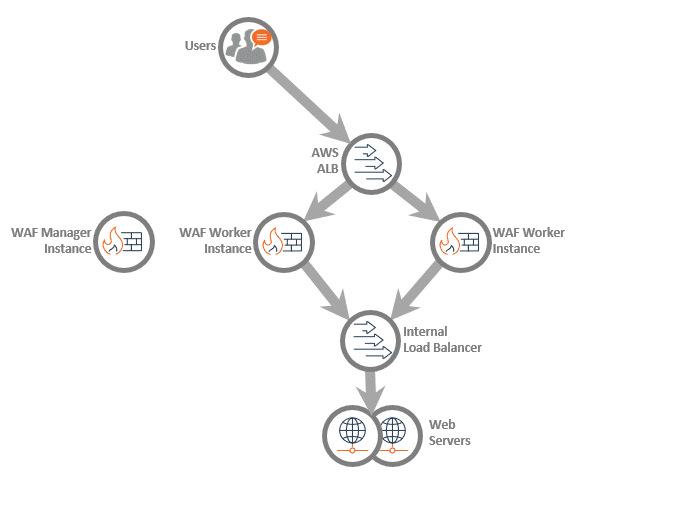
An AWS example
In AWS, Fortra Managed WAF may be configured as a high availability pair (2 WAF instances) or autoscaling. It typically deploys behind an application load balancer (ALB):
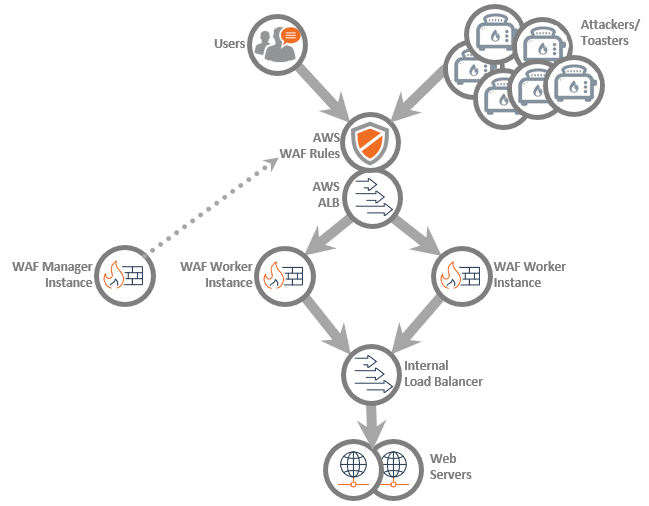
If on-demand DDoS protection is enabled, the WAF can detect and respond to DDoS attacks by automatically creating AWS WAF rules on the ALB:
These rules are controlled and regularly updated by Fortra Managed WAF. By using the AWS WAF as an additional tier of DDoS defense, Fortra Managed WAF can defend against DDoS attacks at a lower cost while leveraging the massive scalability of the AWS cloud infrastructure. Fortra Managed WAF manages the AWS WAF, automatically updating rules to block suspicious IPs and rate-limit connections, providing an additional layer of real-time defense against DDoS attacks before the traffic even reaches the Fortra Managed WAF instances.
Additionally, Fortra Managed WAF can automatically enable CAPTCHA/challenges on the AWS WAF, further limiting the impact of DDoS traffic on legitimate website traffic.
By providing on-demand DDoS protection, Fortra Managed WAF sets a new standard in DDoS protection by activating defenses only when an attack is underway. During normal operations, this approach reduces operating costs and avoids unnecessary CAPTCHAs or challenges. By leveraging the AWS WAF as an additional tier of DDoS defense, Fortra Managed WAF benefits from lower costs and the extensive scalability of the AWS cloud infrastructure.
Ready to learn more? Schedule a demo of Fortra Managed WAF.
Additional Resources:
The Good, the Bad, & the Bulky: How a WAF Defends Against DDoS & Bots