The large-scale ransomware attack WannaCry (WanaCrypt0r, Wcry) has been headline news since May 12th. It began in Europe and quickly spread throughout other parts of the world, impacting more than 100,000 organizations across 150 countries. Initial reports highlighted attacks impacting healthcare organizations—especially the National Health Service (NHS) in the United Kingdom—preventing the ability to treat patients across much of their healthcare network. Since then, the attack has also been reported in Chinese universities, German train station monitors, parking meters, and digital billboards. The damage would have gotten progressively worse, too, if it weren’t for a 22-year-old security researcher in England who activated a “kill-switch” in the attack, effectively halting continued distribution (more on that in a bit).
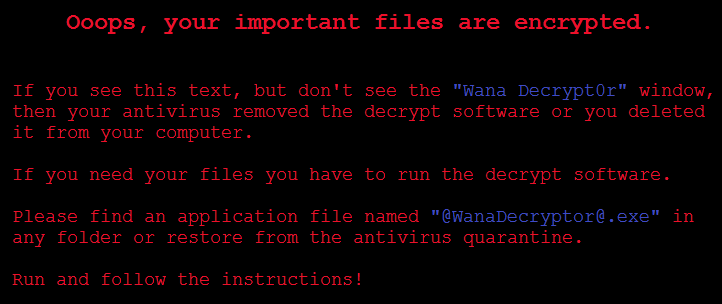
WannaCry (WanaCrypt0r, Wcry) uses a “wormed” malware to self-propagate across networks to target other vulnerable Microsoft Windows machines—especially older variations no longer serviced or issued patches by Microsoft. The initial point of infection and attack vector specifics are still developing, but once a host is infected it is loaded with WannaCry and the DoublePulsar backdoor payload; then, the host starts scanning for other vulnerable hosts for propagation via EternalBlue (Microsoft published a patch for EternalBlue in MS17-010 in March 2017). Once infected, system users will be greeted with the following screens.
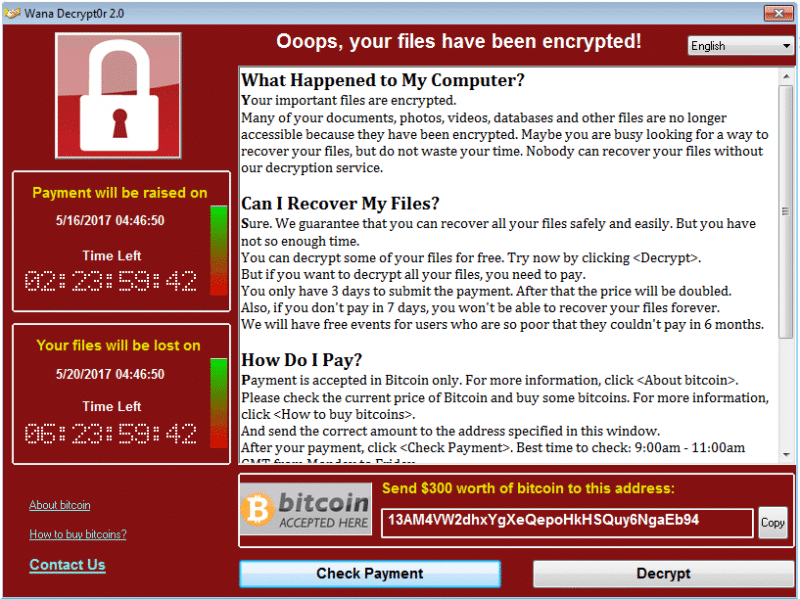
WannaCry Screen 2
WanaCrypt0r has actually been around for months, with limited infections reported. The attack uses WanaCrypt0r 2.0, a combination of the original malware plus EternalBlue and DoublePulsar for self-replication. This new bundle enables it to propagate through a network and infect additional systems running Microsoft Windows without any intervention from users to open an email, click on a link, or open an attachment. EternalBlue and DoublePulsar were two of several potent exploits published in the most recent Shadow Brokers release in mid-April.
Our Alert Logic® ActiveWatch™ team members immediately started researching and analyzing WannaCry since the attack began. We identified the attack methods used by WannaCry and began testing Alert Logic assessment and detection methods (in place since mid-April 2017) related to the ETERNALBLUE and the DOUBLEPULSAR backdoor exploits as well as identification of systems vulnerable to the MS17-010 exploit.
Kill-Switch Activated
The attack was halted on Saturday, May 14, when a cybersecurity researcher activated a kill-switch by registering the single domain used in the ransomware virus. Analysts explain that there is an executable in the ransomware that attempts to connect to a website; it doesn’t download anything, it simply checks for a successful connection. If a connection succeeds, the ransomware “exits,” and effectively doesn’t execute. According to ransomware & malware experts, this means that nothing should happen on any new systems infected with this variant of the WannaCry executable now that a successful connection resolves, for now. Alert Managed Detection and Response team members and industry security experts are warning that the crisis is not entirely over; it is only a matter of time before variants of this attack are deployed without a similar kill-switch.
What can users and organizations do to protect themselves from WannaCry (and possible variants)?
- Patch your systems—all vulnerable versions of Windows are effectively patchable (especially with the update from Microsoft released over the weekend for unsupported systems). The patch for this vulnerability applies to Windows Vista systems and newer, and it can be found in the Microsoft Security Bulletin MS17-010 – Critical security update.
- Run a detailed vulnerability scan against all systems in your environments to identify systems missing the MS17-010 security update.
- Disable SMBv1 in Windows unless it is absolutely necessary. If necessary, ensure it isn’t accessible via open internet.
- Follow client-side hygiene practices and OS vendor advice for baseline security.
- Establish strict needs-based access to network resources and segment networks where possible.
- Backup your data using offline media options as the ransomware worm attempts to infect any connected resources (USB drives, mapped network drives etc.)
- If you are an Alert Logic customer, keep current with our network, web application, scanning, and log alerts.
Regarding patching and upgrades: I know this is not always so simple, especially for large organizations or for application owners that work with layers of third-party add-ons and custom software that sit on top of Windows operating systems. Upgrades, or even patches, require testing for stability, regression testing for features, internal security testing etc., which takes time and requires resources. If you were having problems getting resources approved in your company for testing, patching or upgrades, WannaCry should present a strong argument next time around.
Going forward
There are already numerous claims citing new variants of WannaCry identified in the wild within social media circles. In addition to monitoring these sources for new information, Alert Logic Managed Detection and Response experts will monitor activity across more than 4,000 organizations worldwide to identify new variants or the next new security threat bad guys throw at our customers.