You wouldn’t know it from the onslaught of emails flooding your inbox from companies that “care about your privacy,” but many companies are still scrambling to achieve compliance with the new General Data Protection Regulation (GDPR). In fact, only 7 percent of companies surveyed in our new 2018 GDPR Compliance Report said they were on track to be compliant when the GDPR came into force on May 25, 2018. According to the companies surveyed, the primary challenges to achieving GDPR compliance are:
- Lack of expert staff with critical skills (43 percent)
- Lack of budget (40 percent)
- Limited understanding of GDPR regulations (31 percent)
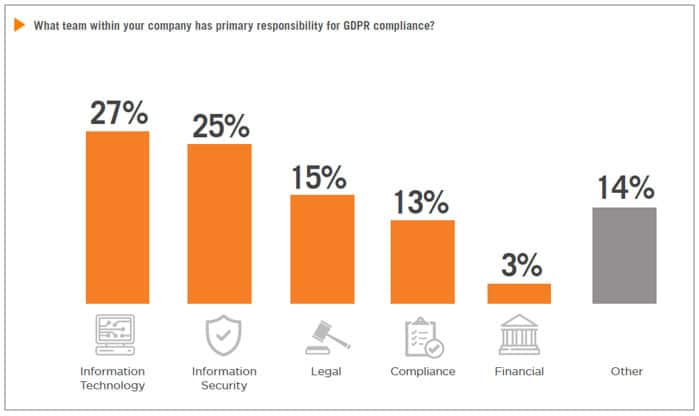
What makes this more interesting is the break-out of company responsibilities/ownership for GDPR compliance.
This is interesting to me because most of the GDPR concerns organizational measures related to processes, policy, and documentation—not IT Security. Unlike other security compliance mandates such as PCI DSS Compliance or ISO-27001, the official GDPR doesn’t include a list of detailed security controls for IT professionals to use as a punch list. Yet, over 500 of the surveyed companies said that the #1 challenge to achieving compliance was lack of expert staff, AND that 52 percent of those companies assigned primary GDPR ownership to IT Security teams (27 percent IT, 25 percent InfoSec) who are already stretched and facing a shortage of skilled workers. No wonder they cite a lack of expert staff as their primary challenge.
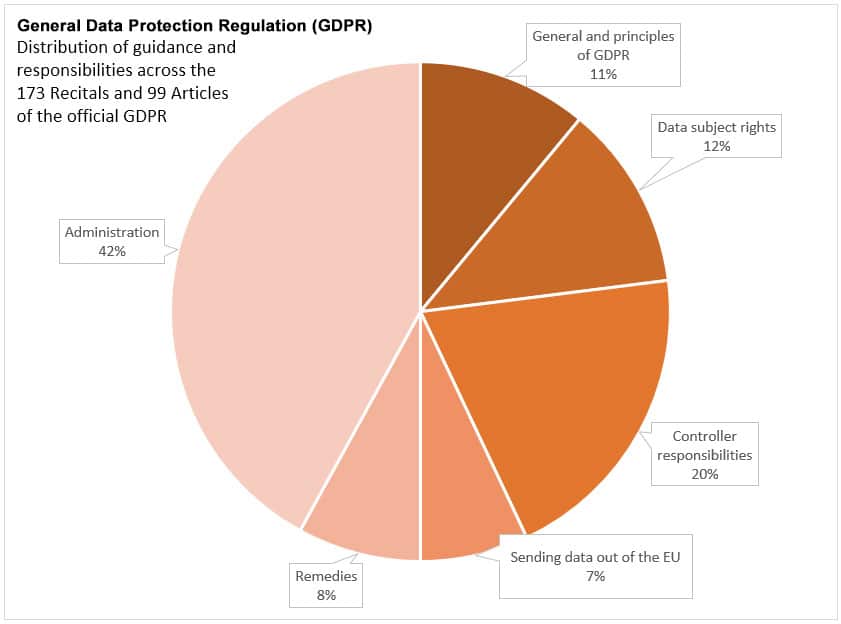
Even if properly staffed and funded, IT security professionals can only address a small percentage of the requirements found in the GDPR. In fact, out of the 173 Recitals and 99 Articles in the GDPR, only a few include provisions for responsibilities that fall within scope of what most IT security professionals can address. There is a lot of work that can only be done by other teams/roles in a company for an IT security professional to properly address GDPR requirements.
GDPR Article 32 and the IT Security Professional
Most security professionals will focus on Article 32, which represents the main provision requiring technical measures for data security. Other GDPR Articles to address include Articles 24, 25, 28, 33, 34 & 35—that establish risk-based design principles, and security related obligations and processes enabled by Article 32 (like breach notifications).
Article 32 is the big one for a security professional. It provides a risk-based approach to implementing “appropriate technical and organizational measures to ensure a level of security appropriate to the risk.” It doesn’t include any details, only “Taking into account the state of the art…,” which basically means you should use the appropriate technology found to be used by peers, other Industries, and other compliance standards to keep protected data secure, such as:
- Identify and fix vulnerabilities and risky configurations that attackers can exploit
- Encrypt protected data when it cannot be pseudonymized
- Monitor all network traffic to identify potential threat activity
- Inspect all web application traffic to detect suspicious activity
- Collect log data from all systems to identify suspicious behavior, and enable post-compromise forensics
This is just a simplified, high-level list, and without a clear understanding of the type of data you need to protect, where it lives, and how it is processed, a security professional can only do so much to keep protected data secure. More importantly, even if a security professional has all this information and a budget to implement any security control available, an organization can still be far from GDPR compliant without similar efforts from other teams in a company (legal, finance, marketing, operations…yeah, I’m talking to you).
Stay tuned. My next blog post I’ll go into more detail on Article 32, existing frameworks that can be used as guidance, and its relationship with Articles 24, 25, 28, 33, 34 and 35.
[Related: Read our report on GDPR Compliance in the EU]
[Related: The Top 8 Data Security Best Practices]