Defining XDR
What is XDR? It is a multi-faceted threat detection and response technology. It functions by gathering and correlating data from diverse telemetry sources including endpoints, servers, apps, clouds, and networks. This broad spectrum of coverage enhances an organization’s visibility into its cyberattack surface. The primary objective of extended detection and response is to empower organizations to augment visibility, expand coverage, enhance operational efficiency, and ultimately fortify their overall security posture. XDR solutions empower cybersecurity professionals and SOC teams to interpret data from point sources more effectively and provide insights for responding to potential threats using advanced technology.
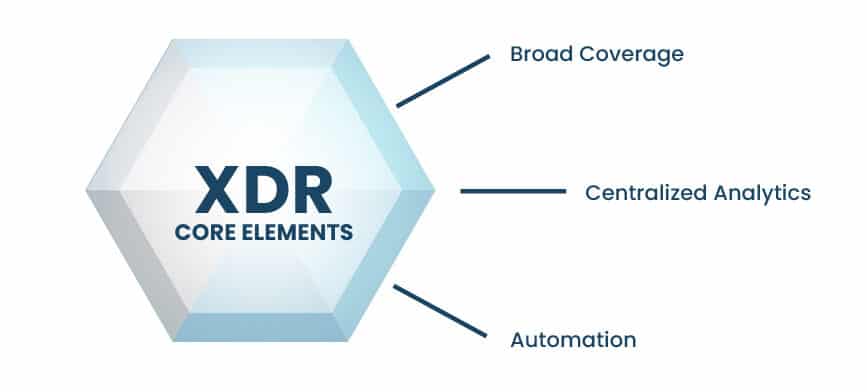
While the definition of XDR has evolved in recent years, the commonly accepted core elements of an XDR solution include:
Broad Coverage | Ability to ingest from multiple telemetry and data sources including:
- Endpoint and/or EDR technologies
- Network
- Intrusion detection systems (IDS)
- Security information and event management (SIEM)
Centralized Analytics | Ability to analyze and correlate data. This can be done via machine learning (ML), AI, and in-house/proprietary analytics tools
Automation | Ability to utilize playbooks and workflows to automate repetitive and/or common actions
The confusion surrounding the definition of extended detection and response stems from the various approaches used to implement it. Originally, EDR vendors expanded their telemetry sources by adding another, claiming XDR capabilities. Meanwhile, some vendors adopted XDR by integrating SIEM technology with automated response systems. Today, XDR can be implemented in many different ways. Until the industry reaches a consensus on a standardized definition, extended detection and response security solutions will continue to evolve in response to the growing complexity and dynamism of the threat landscape.
How XDR Works
XDR ingests data from diverse sources, including endpoints, SIEM, analytics, logs, IDS, and third-party feeds. It systematically analyzes the data by establishing correlations between the sources, identifies behaviors based on known threats, and may give visibility to unknown activity. Harnessing threat intelligence, extended detection and response prioritizes and informs on what activities poses the greatest risk. Security analysts enhance this information by triaging high-risk activities, providing valuable insights, and offering remediation guidance to customers.
To maximize the benefits of implementing an extended detection and response solution, a high level of security expertise and resources is essential to achieve the desired outcomes of this strategy. You can accomplish this by using in-house dedicated security resources or leveraging a managed XDR service.
Core Capabilities of an Effective XDR Solution
A robust solution requires a core set of capabilities outlined below. While the delivery methods for these capabilities may significantly differ among vendors, they collectively represent the essential elements needed for a solid foundation.
Broad Coverage
- Unified console for visibility across the environment
- Visibility and coverage extended via integration with network, endpoint, applications, servers, and end user devices
- Integration with existing third-party EDR, network and identity tools
- Logs ingest and data collection from a wide range of sources
Centralized Analytics
- Behavioral and anomaly-based analysis
- Rule/signature-based analysis
- Machine learning
- Incident correlation
- Threat scoring and prioritization
- Unified threat console
Automation
- Wizard-based workflow templates and playbooks
- Broad response coverage – endpoints, firewall, network, and identity
- Support for third-party network and identity tools
 What is Managed XDR?
What is Managed XDR?
A managed option is essential for organizations that lack the internal resources or expertise to effectively manage their extended detection and response solution, despite being offered by only a limited number of vendors. Managed XDR should include:
- 24/7 monitoring
- Designated security analyst
- Threat hunting (including emerging threats)
- Incident validation
- Security investigation
- Analysis, triage, and investigation
- Financially backed SLA
Learn more: Is a managed XDR solution right for my organization?
Benefits of XDR
Extended detection and response offers centralized, comprehensive visibility and coverage across multiple products and telemetry sources. It brings several key benefits, enhancing organizational efficiency and scalability, which are crucial for strengthening your security posture.
Greater visibility and context
XDR gives you a holistic view of potential threat activities that may have infiltrated your environment without detection. By leveraging a diverse set of telemetry sources and employing thorough threat monitoring and analysis, security analysts gain a more comprehensive understanding of potentially hazardous activities within the environment. This enhanced perspective allows for better-informed decision-making regarding security measures.
Response automation
Organizations can enhance operational efficiency and minimize the need for manual review in response actions by harnessing the power of response automation. Integrating this capability into any extended detection and response solution enables organizations to use streamlined response workflows and playbooks to automate actions across network, endpoint, and cloud environments. As a result, time-to-resolution significantly decreases, allowing for swift responses to emerging threats. Collaboration with a global SOC further strengthens this efficiency, providing expert-guided insights to support security teams facing resource constraints.
Risk prioritization
Security analysts often face an overwhelming number of alerts, limited context, and difficulty prioritizing the riskiest activities. XDR security automates analysis and correlation to identify and prioritize risks based on known threat behaviors, summarizing them by risk priority. This approach enables teams to quickly address and resolve the most critical threats.
Reduced Mean-Time-to-Detection
Advanced cyber tactics, such as phishing attempts, cloud hacks, and compromised application access, can allow malicious activity to go undetected in your environment. The longer a compromise goes undetected (known as dwell time), the greater the risk of substantial financial and brand-related consequences. XDR security improves response times by continuously monitoring a broad range of telemetry sources that combine prevention and detection technologies. This proactive approach ensures quick identification of attacks, reducing both the time and impact of the attack.
Enhanced security posture
Establishing and maintaining a robust security posture requires organizations to consistently stay ahead of the evolving threat landscape. Key components, such as comprehensive visibility, extensive coverage, continuous 24/7 monitoring, regularly updated threat intelligence, and proficient security expertise, are crucial to ensure successful management. Extended detection and response reduces the burden of organizations having to address these elements on their own.
XDR vs. EDR, MDR, SIEM, SOAR and More
XDR vs EDR
What’s the difference between XDR and EDR?
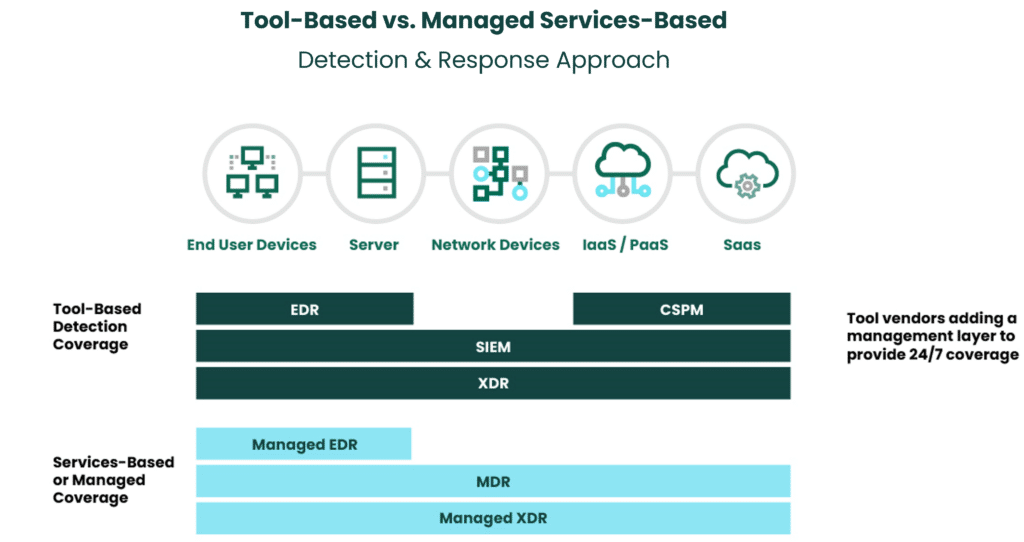
Endpoint Detection & Response (EDR) is a commonly utilized prevention tool with visibility limited to endpoint telemetry sources. It is commonly used alongside antivirus (AV) tools, though achieving comprehensive coverage and desired security outcomes may necessitate its conjunction with additional security tools. It can be delivered as a tool or managed service, and may include investigations, threat hunting and response capabilities when part of a managed service.
EDR is a great starting point and should be considered in any security strategy. Organizations may prioritize prevention technologies in their strategy, and EDR can address that requirement. However, as long as the threat landscape continues to become more complex and threat actors become more sophisticated, prevention-alone will not suffice. Organizations would be remiss if they did not prioritize prevention and detection in their security strategies. The prevention side of a security strategy addresses the need to minimize an attack. Detection side of the strategy ensures you can more quickly identify, analyze and respond to threats to reduce the impact of the threat when it occurs.
XDR vs MDR
What’s the difference between XDR and MDR?
XDR comes in many flavors and can range from a tool with coverage limited to 2-3 telemetry sources up to a fully managed XDR service that provides the technology, coverage and security expertise.
If your team is comprised of highly skilled dedicated security experts, you have the resources and the time to manage, analyze, triage and address the volume of incidents and threats observed in your environment, an unmanaged extended detection and response solution may work well for your organization. The success of this approach will be dependent on selecting the technology that best integrates with your existing security tool stack and that can correlate and provide actionable insights from the disparate tools.
While unmanaged extended detection and response works for some businesses, it might not be right for your organization due to lack of core resources mentioned previously. To get the desired value out of an XDR solution requires a level of security knowledge and/or expertise. Most organizations don’t have these in-house resources. Keeping an eye on XDR and countering the threats it raises can be expensive and complex. You still need to hire security specialists who can act on potential threats. In this case, a managed extended detection and response solution may be the best option. Objectively assessing the capabilities and limitations of your team against the desired security outcomes will help you make an informed decision if unmanaged or managed XDR is best for your organization.
If you’re considering MDR as an option, it’s most effective as a complement to extended detection and response. MDR is part of the evolution of detection and response technologies, with its capabilities fully included into the XDR solution.
Key things to consider:
- What do you need to protect? Whether you choose MDR or XDR, ensure the coverage extends across a wide range of telemetry sources. Keep in mind that some tool vendors will provide a limited range of telemetry visibility.
- Do you have the resources and expertise to effectively manage the technology and get actionable insights from it? If not, a managed service is recommended. Many detection and response vendors only offer tools. Without the security expertise to make sense of the data, you will be hard pressed to get the security outcomes you seek.
- What does your long-term security strategy look like? If you are leveraging existing security tools and technology (e.g., EDR, SIEM, SOAR), you’ll want to ensure that the selected detection and response platform can seamlessly integrate with your existing investments and provide the flexibility and scale to adapt as your business grows.
XDR vs SIEM
What’s the difference between XDR and SIEM?
A Security Information and Event Management (SIEM) system functions as a data collection tool, extracting information from diverse sources like workstations, application logs, servers, network devices, firewalls, and IDS. While effective in handling extensive data volumes, its capacity to identify and rank risk activities necessitates augmenting it with complementary security tools. It does require additional security technology to prioritize and analyze the massive data logs. A SIEM requires significant human resources to decipher the data, a challenge most organizations are trying to overcome. Organizations looking to gain contextual awareness and/or real-time analysis of activity of their environment will not get those outcomes with a SIEM.
XDR vs SOAR
What’s the difference between XDR and SOAR?
SOAR provides an effective way for organizations to streamline processes and automate tasks required when observing and detecting security incidents. To get the best outcomes from a SOAR tool, it is crucial to integrate it with other security tools. In general, SOAR and automated response capabilities should be a core element of an XDR solution. As highlighted earlier, the ability to automate response actions is an essential criterion for getting security value from extended detection and response. The response actions within XDR should address common use cases such as host isolation.
Fortra XDR, Delivered by Alert Logic
Fortra XDR seamlessly integrates industry-leading managed detection and response capabilities with a lightweight Fortra agent uniquely designed to target endpoint telemetry. This groundbreaking solution extends visibility across the entire IT estate including end user devices, network and cloud environments, as well as integration with third-party identity and EDR sources. The benefits of incorporating Fortra XDR into your cybersecurity strategy are numerous, including:
- 24/7 threat management and security expertise delivered by a global SOC team
- Services cover all your networks, applications, and endpoints, whether they’re in hybrid, on-premises, or cloud environments.
- 15-minute escalation SLA (critical and high incidents)
- SOC threat hunting of known and unknown threats
- SOC-deployed response actions performed for the customer
- Automated response (SOAR) for core use cases (such as host isolation)
- Threat intelligence leveraging insights from Fortra Threat Brain
Fortra XDR empowers organizations to leverage a diverse array of detection and response sources, feeds, and tools. This enables them to efficiently identify, analyze, correlate, and promptly address potential risks. Fortra XDR integrates advanced analytics and threat intelligence, ensuring organizations are always prepared for emerging challenges in the ever-evolving cyber landscape.
Ready to explore how Fortra XDR can secure your IT estate?
Frequently Asked Questions
Is a managed XDR solution right for my organization?
When considering a managed extended detection and response option, there are two key factors to keep in mind:
- Assess whether the solution offers the right detection and response capabilities to meet your organization’s specific goals.
- Objectively evaluate whether you have the necessary internal resources and expertise to effectively manage and extract actionable insights from the existing tools and technologies in place.
Evaluating XDR requires a thorough review of current market solutions in detection and response, such as SIEM, EDR, and MDR. Understand their capabilities, strengths, and weaknesses to make a well-informed decision. Then, align these insights with your broader security strategy and goals. For a quick overview of how each of these options can support your security outcomes, check out the blog on Understanding XDR, EDR, and MDR.
Managed vs Unmanaged: To determine if you need managed or unmanaged extended detection and response, objectively evaluate what your team and organization can realistically handle. Consider the following:
- Where are you from a security maturity perspective?
- How important is it to you to own security controls?
- What level of security controls do you need/want to own?
- Do you dedicate resources to security?
- Are you able to effectively manage the tools and processes in house?
- Do the team have the knowledge, bandwidth and time to monitor your environment 24/7?
If I choose XDR, how much of my existing security stack can I leverage?
Extended detection and response is optimized to integrate with your existing IT investments. For example, if you currently utilize a third-party EDR solution, the solution should be seamlessly integrated into the platform. XDR’s goal is to help organizations achieve efficient, scalable, and comprehensive coverage. The ability to do so requires the flexibility to leverage existing investments and get more value of them.
Is there a Gartner XDR Magic Quadrant?
As of January 2025, Gartner has not published an XDR Magic Quadrant. Gartner Peer Insights does include “Extended Detection and Response” as one of their Enterprise Software Categories, which may suggest that an XDR Magic Quadrant will surface in the future. Today, extended detection and response capabilities are discussed as “emerging capabilities” within the Gartner Magic Quadrant for Endpoint Protection Platforms.

 What is Managed XDR?
What is Managed XDR?