Why Choose Managed Detection and Response?
When internal resources or cybersecurity expertise fall short, Managed Detection and Response (MDR) fills the gap. Gain the technology, experts, and proven processes needed to detect, respond to, and mitigate threats — delivering the comprehensive protection modern environments demand
24/7
Security Monitoring
24/7
Threat Intelligence from the Fortra Threat Brain
20+
Years of Security
Expertise
360°
View of Your
Exposures
3.3m+
Servers, Containers and Endpoints Monitored
45+
Threats Identified Monthly through Structured Threat Hunting
Proven MDR Solutions
Cybercriminals are more successful at exploiting security vulnerabilities than ever. To combat this challenge, an effective MDR solution must stay one step ahead. That’s why comprehensive prevention and detection is at the heart of Fortra’s Alert Logic Managed Detection and Response. With Alert Logic MDR, you can expect:
- Proactive threat hunting to stay ahead of evolving risks
- Cyber-risk experts delivering in-depth threat insights and analysis
- Rapid threat detection and automated, immediate response
- Comprehensive visibility across your entire IT landscape
- Real-time dashboards tracking threats, risk, vulnerabilities, remediations, coverage, and system health
- A customizable MDR solution for your unique business needs
- Enhanced security compliance strategy
Check out this quick MDR video
Managed Detection and Response: Key Components
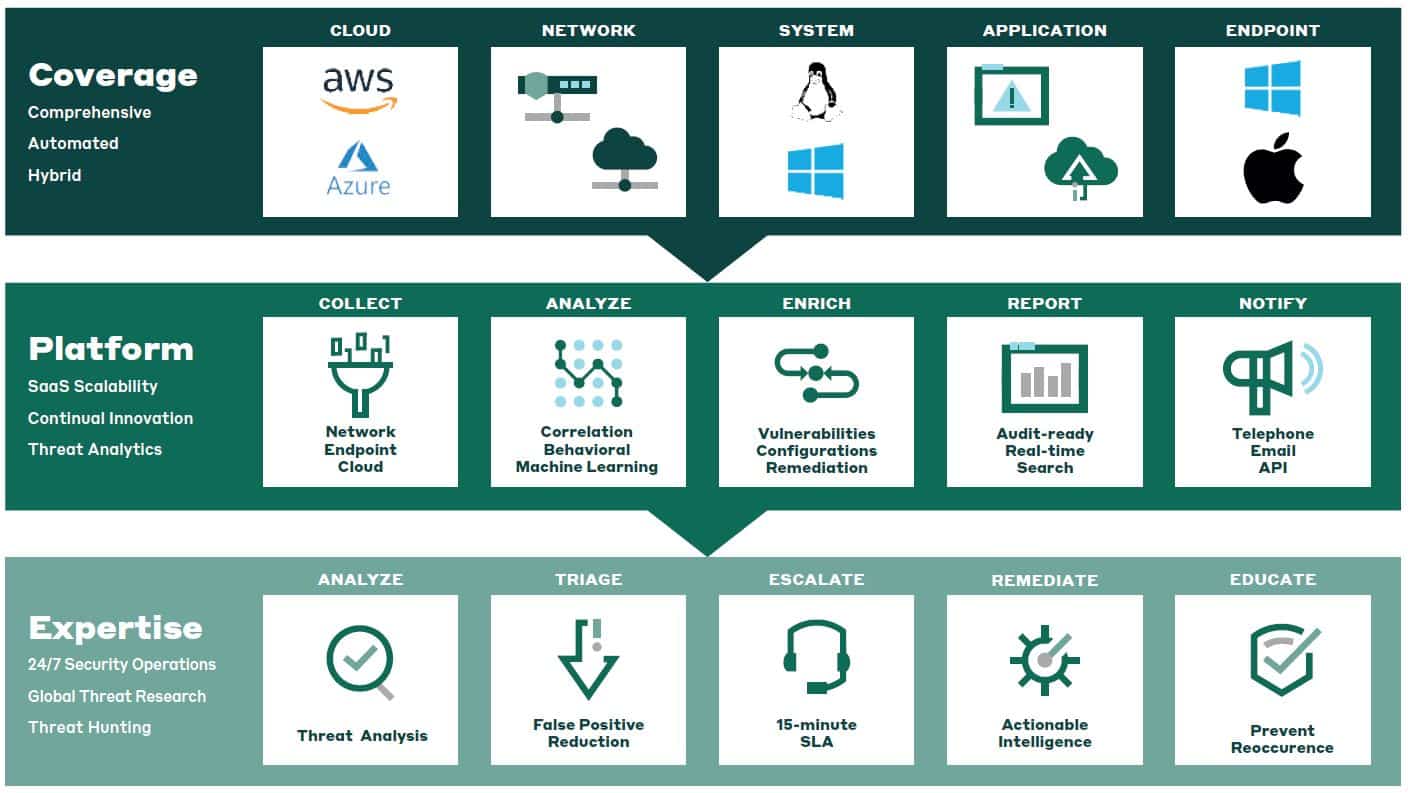
COMPREHENSIVE COVERAGE
Whether you’re aiming to extend protection to SaaS applications, gain insights into network security controls, or integrate with third-party security solutions, your detection and response platform must cover the entire attack surface. Alert Logic MDR uses data feeds from your environment — including log data, assets, network telemetry, endpoints, and outputs from infrastructure and security systems — to ensure comprehensive visibility and security coverage.
SECURITY FOR ANY ENVIRONMENT
Effectively manage your security posture with MDR solutions that run in all public cloud, private cloud, hybrid cloud, and on-prem environments. Our cloud-native platform is designed for seamless integration with existing IT infrastructure, being both scalable and flexible, changing as your organization does.
MANAGED DEFENSE IN DEPTH
It’s no small task to collect, store, analyze, and report at scale across assets, logs, events, network telemetry, endpoint, third-party telemetry, and user and file access. Alert Logic MDR feeds all that critical data into our platform, turning the data into valuable information for our security teams and customers to gain a full understanding of the security posture and threats posed to customer systems.
CONTINUOUS CUSTOMER VALUE
Every step of your experience with Alert Logic is focused on providing continuous value throughout the customer lifecycle. From staying up to speed on the latest threats, to simplifying your onboarding experience to delivering ongoing continuous innovation, our goal is to help you successfully achieve your security goals and improve your security posture.
See Alert Logic in Action
Core MDR Features and Capabilities
Delivering unrivaled threat intelligence, SaaS security, and 24/7 managed expertise
to continuously keep your assets in any environment secure.
24/7 Threat Monitoring
Threat actors don’t adhere to standard business hours, so around-the-clock monitoring to quickly identify and remediate threats before real damage is done is critical.
|
Monitoring features include:
|
|
|
Response Automation (SOAR)
Organizations looking to enhance their response capabilities can take advantage of embedded SOAR, enabling them to adopt automation at their own pace, providing flexibility to balance full automation with human-guided response.
- Wizard-based Workflow Templates
- Broad Response Coverage – Endpoints, Firewall, Network and Identity
- Automated Response Mobile Application
Threat Intelligence and Analytics
As threats constantly evolve, the technology to detect them must adapt continuously. Our security experts and researchers continuously perform complex threat analysis, gathering intelligence from the security community and multiple telemetry points to identify unknown threats.
- Continuous Learning Engine
- Log Analysis
- Behavior Analysis
- Rule-/Signature-based Analysis
- Machine Learning
- Anomaly-based Analytics
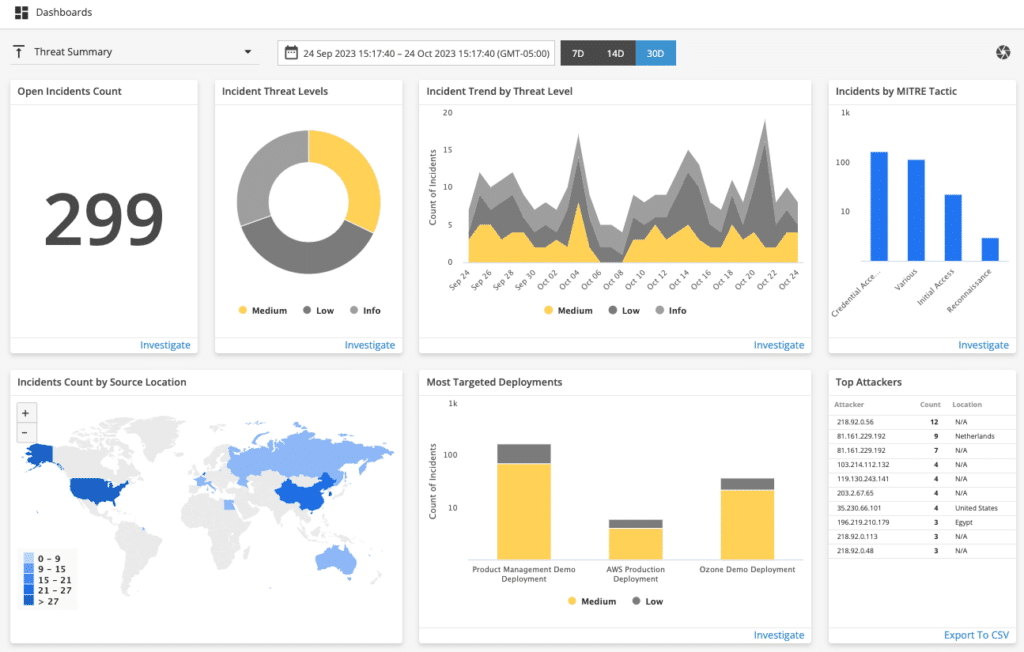
Real-time Reporting & Dashboards
Real-time reporting and dashboards provide convenient access to summary visualizations with drill-down features to interact with detailed data and specific capabilities. This easily accessible information enables organizations to quickly understand the state of their environment, prioritize the riskiest security events, and support compliance requirements.
- Compliance Reporting — PCI, HIPAA, SOC2, NIST, HITRUST, GDPR
- CIS Benchmark Reporting
- Asset Discovery and Visualization
- Real-time Dashboards – Threats, Risk, Vulnerabilities, Remediations, Coverage and Health
Security Operations Center and Expertise
Organizations that lack in-house security expertise or are looking to augment their security teams can leverage our global SOC analysts and experts to provide insights and remediation guidance on known and unknown threats.
|
SOC features include:
|
|
|
Stop Threats in Their Tracks with MDR
As organizations have increased their adoption and reliance on detection and response technologies, new cybersecurity challenges have emerged that many organizations struggle to manage. Among the top cybersecurity challenges facing organizations today are:
Visibility
Lack of visibility is one of the biggest challenges organizations face, creating an ideal environment for threat actors who exploit what you can’t see. Whether your infrastructure is on-premises, cloud-based, or hybrid, maintaining a clear and comprehensive view across endpoints, networks, cloud workloads, and SaaS applications is critical. With an average of 258 days to identify and contain a threat, prioritizing unified visibility is essential to mitigating risks and reducing dwell time. Learn more about visibility
Ransomware
Ransomware remains one of the most formidable cybersecurity threats, with attackers constantly advancing their tactics to breach systems and networks with greater sophistication. To defend against these evolving threats, organizations must adopt a robust security posture that minimizes the risk of a successful attack. Learn more about ransomware
Addressing Pre- and Post-Breach Concerns
Preventive tools help reduce attack risks, but they fall short against today’s increasingly sophisticated threats. A truly effective solution must cover the entire kill chain, ensuring robust protection that not only mitigates threats before they strike but also strengthens response and recovery after a breach, delivering real security outcomes, not just promises. Learn more about breaches
Compliance
The ever-evolving landscape of security laws and standards makes policy mapping a daunting challenge — especially without dedicated experts on your team. Compliance isn’t just a box to check; it’s a complex web of regulations designed to protect organizations, individuals, and entire industries from breaches and data loss. Without the right expertise, staying ahead of these shifting requirements can feel impossible. Learn more about compliance
24/7 Security Expertise
Cybersecurity threats don’t follow a 9-to-5 schedule, and neither should your defense. If your organization lacks the resources for round-the-clock security monitoring, you’re exposed to risk. Hiring internally? You’re not alone in facing the global cybersecurity talent shortage — businesses worldwide are struggling with critical resource gaps. The demand for skilled cybersecurity professionals is surging, yet the labor market simply isn’t keeping up. Learn more about talent shortage
Securing the Cloud
Whether your business runs only in the cloud or a hybrid environment, securing workloads is a critical challenge. Misconfigurations, limited visibility, and a lack of expertise create openings for cybercriminals to inflict serious damage. Gaining a comprehensive view of your entire attack surface is essential to minimizing risk and fortifying your defenses. Learn more about cloud security
MDR SERVICE AT-A-GLANCE
MDR Enhances Cyber Resilience
The Value of Our MDR Service
Partnering with Alert Logic’s security experts ensures your environment stays protected — so you can stay focused on your customers and keep operations running smoothly. Key benefits of Alert Logic Managed Detection and Response include:
Scalable MDR Platform
Our MDR platform and team of experts collect network traffic from more than 140 billion log messages every day, giving you outcome-based security coverage against vulnerabilities and threats. We analyze and provide a curated set of content in a single location, so your organization can easily manage your security posture. Our services cover all your networks, applications, and endpoints, whether they’re in cloud, hybrid, or on-premises environments.
Security Insights at Your Fingertips
Alert Logic’s MDR platform provides a dashboard view of all alert information and analysis from our team of security experts. You get access to real-time information on risk, vulnerabilities, investigations, remediation activities, configuration exposures, and compliance status. Easily navigate the dashboard to rank your security threat priorities and focus your time and resources on threats that require more attention. Our dashboards also provide user-friendly visualizations of risk to share with your executive leadership teams.
MDR Resources