Protect Against Multi-Layered Strategies
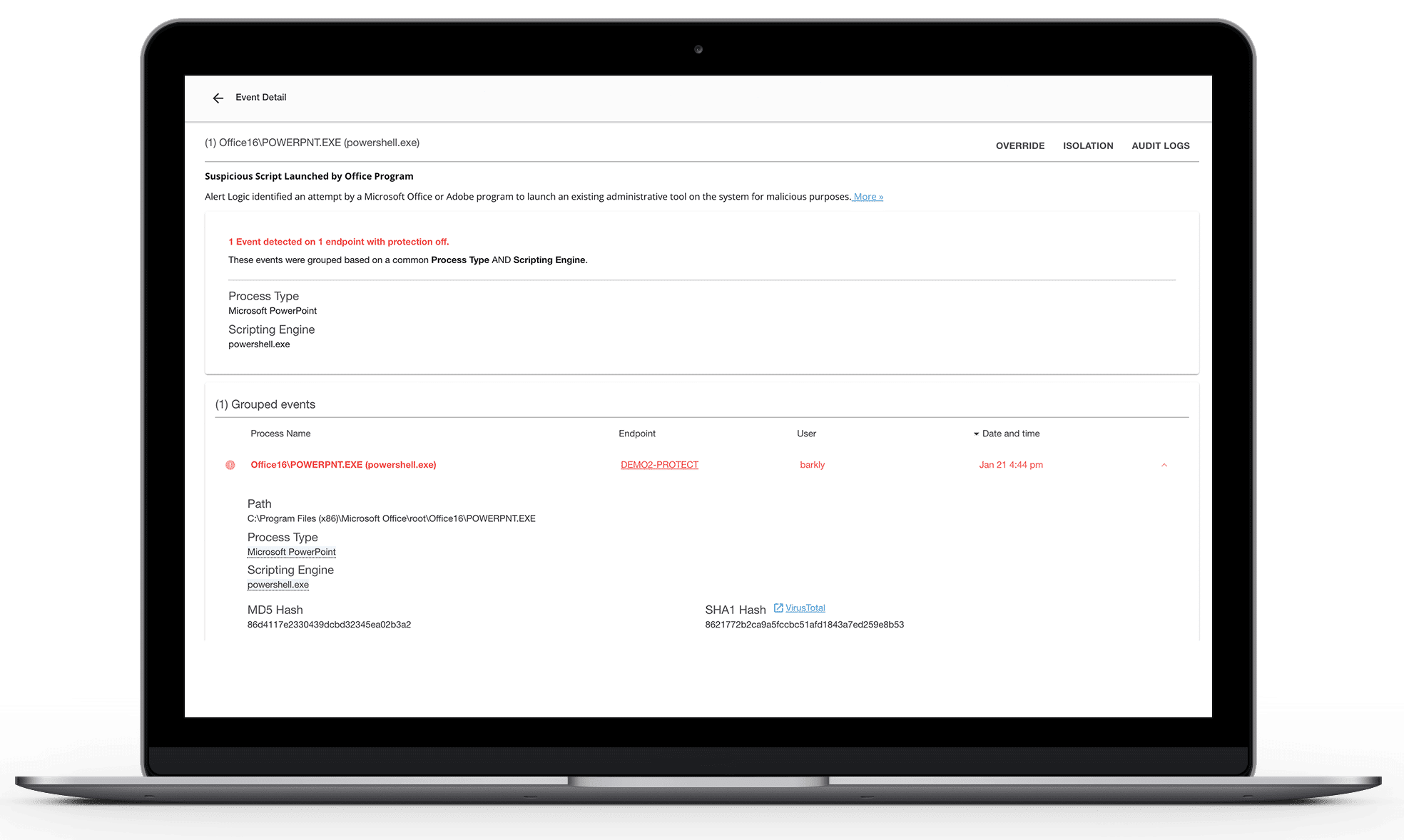
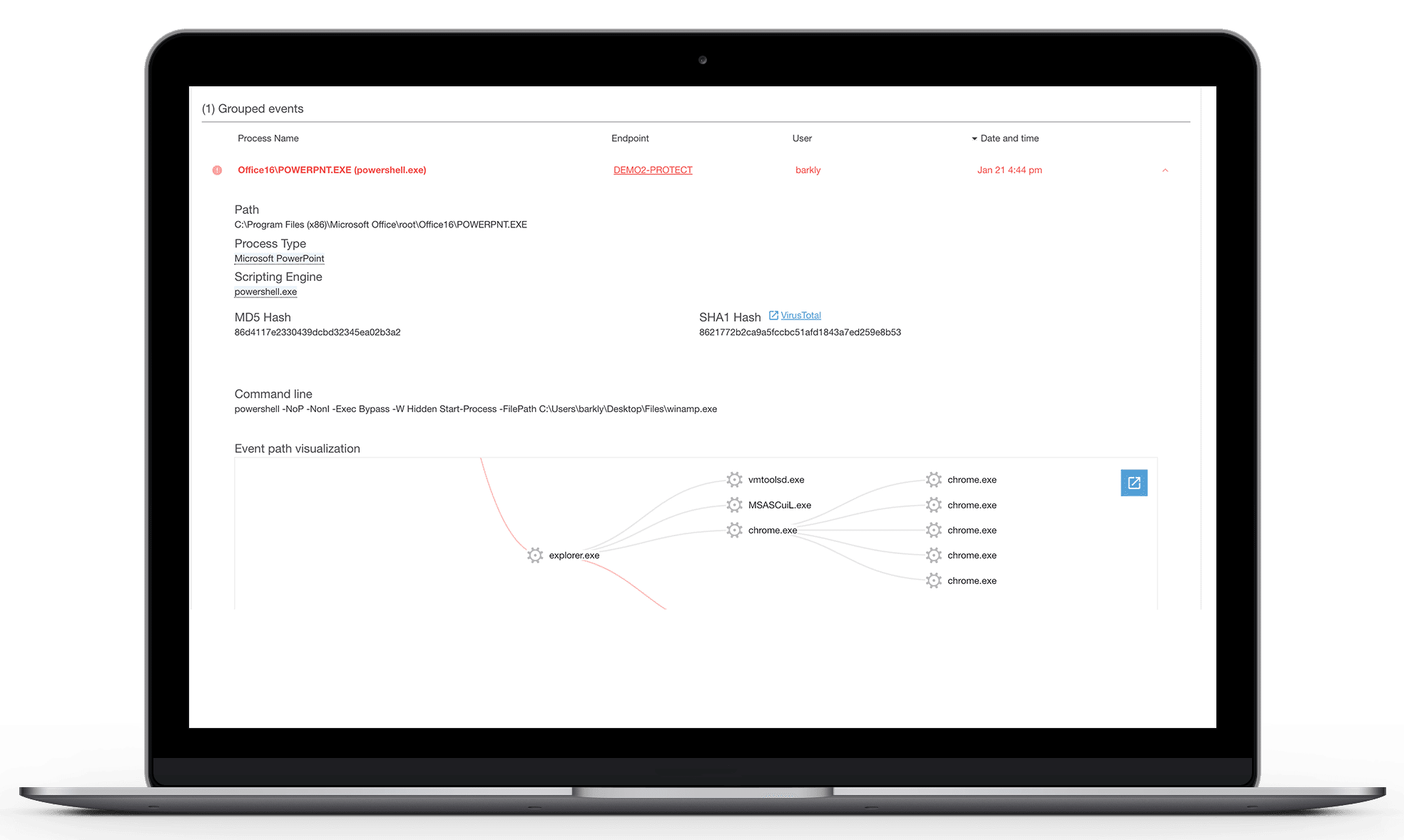
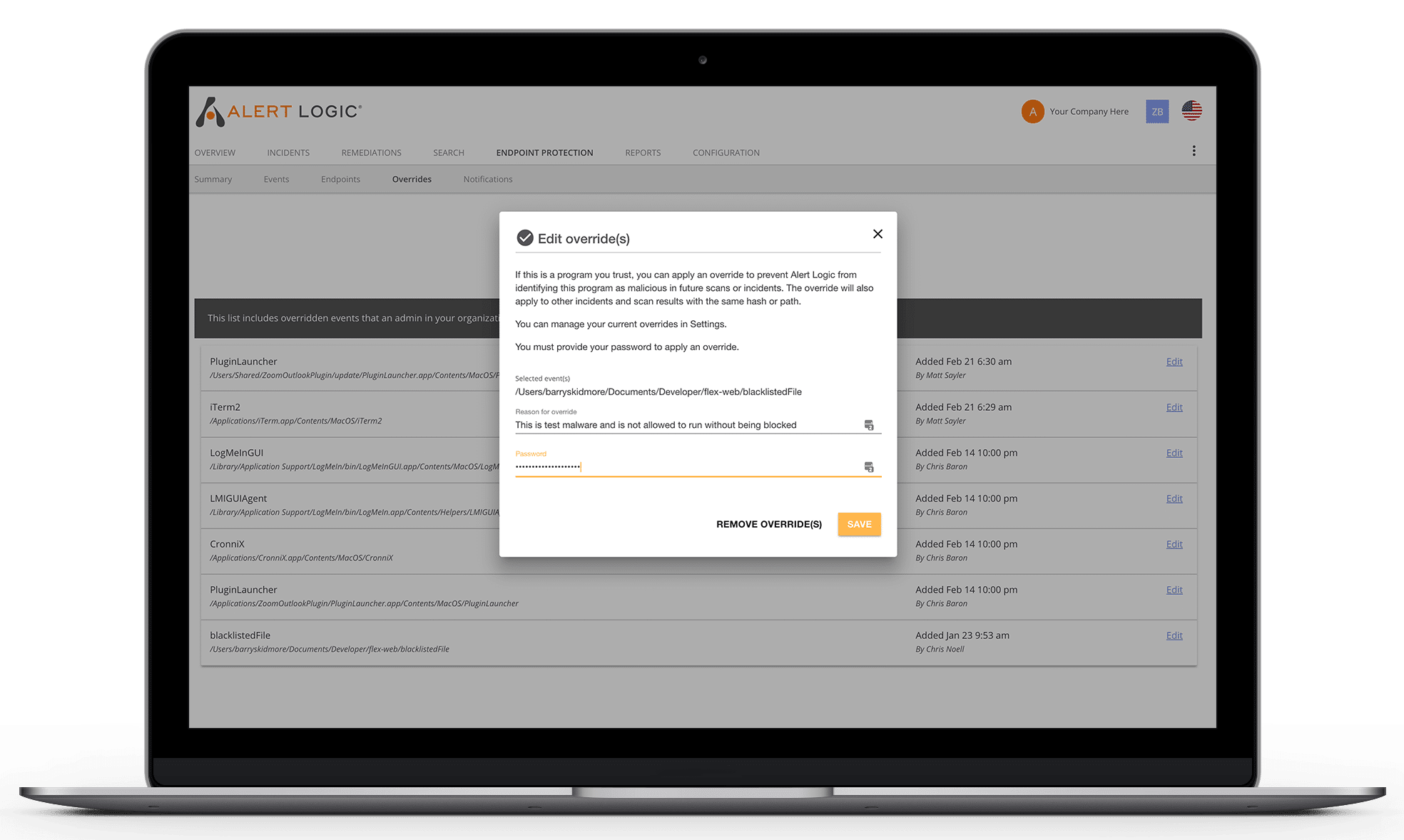
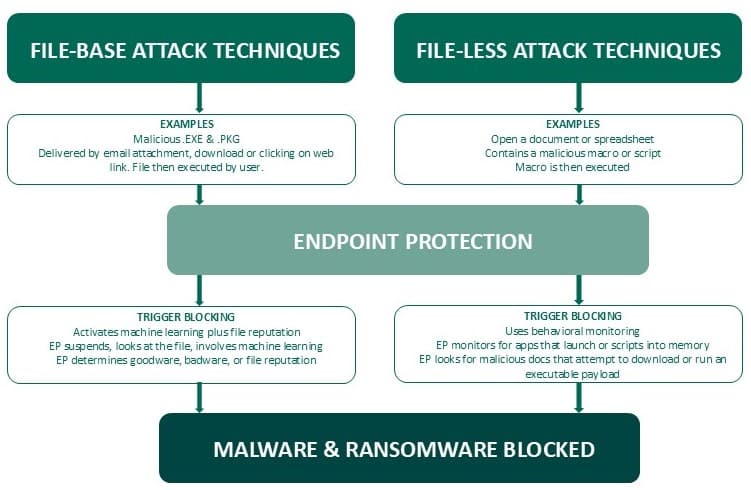
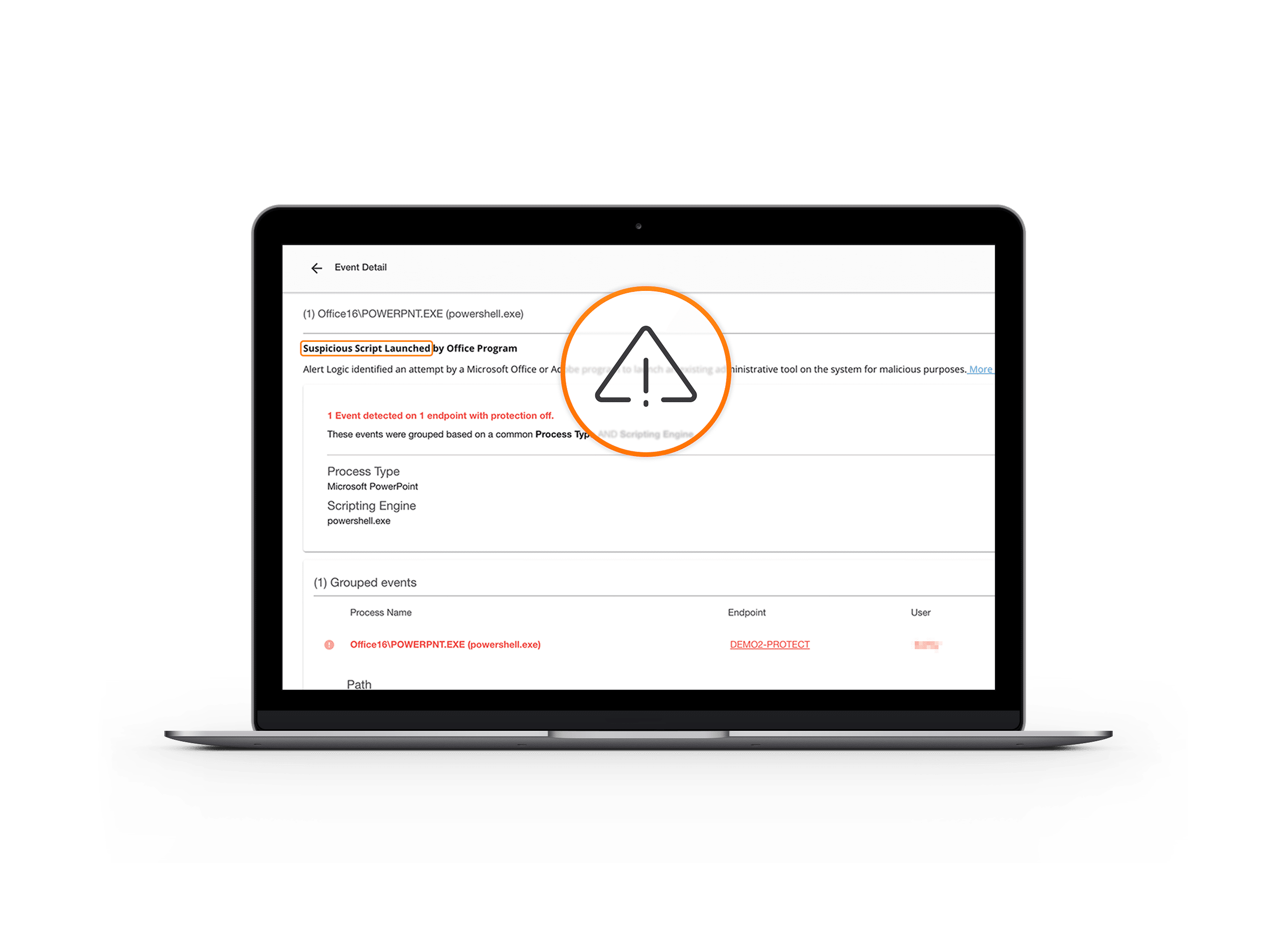
Cybercriminals use a range of techniques to infiltrate and compromise systems, targeting endpoints to deliver malicious payloads with devastating effect on both Windows and macOS platforms. Endpoint detection empowers you with advanced, multi-vector monitoring and rapid isolation, spotting and neutralizing threats early before they can cause harm. This proactive defense prevents attacks in real-time, stopping them before any damage is done. Our managed security services seamlessly complement your existing antivirus tools, adding an extra layer of robust protection.
With Alert Logic, safeguard sensitive data against multiple attack techniques:
- Use machine learning to outpace attackers and zero-day attacks
- Detect malicious tactics and ransomware in real-time
- Isolate compromised devices
- Gain deep visibility across endpoints
- Secure endpoint devices whether online or offline
- Designed to be fast with low overhead (1% CPU utilization)
- Identify emerging threats faster with signature-less technology
Secure Endpoints With
Machine Learning & Analytics
Alert Logic Solution Benefits
Alert Logic provides a robust, cost-efficient solution that seamlessly integrates full asset visibility, accurate vulnerability assessments, and critical threat detection and response. With Alert Logic, organizations gain broader detection capabilities and accelerate their response times — all while minimizing effort and reducing costs.
SECURITY PLATFORM
- Asset discovery
- Extended endpoint protection
- Vulnerability scanning
- Threat monitoring and visibility
- Intrusion detections
- Security analytics
- Log collection and monitoring
THREAT INTELLIGENCE
- Threat Risk Index
- Verified testing 2.1 million + web application attacks
- Remediation guidance
- Attack prevention capabilities
- Extensive log search capabilities
- User behavior anomaly detection
- Event insights and analysis
- Threat frequency, severity, and status intelligence
- Comprehensive vulnerability library
EXPERT DEFENDERS
- 24/7 SOC with incident management, escalation, and response support
- PCI DSS 4.0 scanning and ASV support
- Service health monitoring
- Incident response assistance
- Threat hunting
- Support with tuning strategies, customized policies, and best practices