Quickly Detect Network Intruders Across Your IT Environments
Safeguard your business with Alert Logic’s award-winning managed security services. Our advanced network intrusion detection system (IDS) delivers comprehensive protection for your containers, applications, and entire infrastructure — whether hybrid, cloud, or on-premises. With always-on threat monitoring, we rapidly identify intrusions, reducing attacker dwell time and minimizing potential damage to your environment. Stay secure with faster detection and smarter defense.
Our solution empowers organizations to identify critical threats, including lateral movement, brute force attacks, privilege escalation, ransomware, and command-and-control exploits, while providing robust detection capabilities. By collecting and analyzing network traffic across hosts, it ensures comprehensive threat visibility. Additionally, our advanced container security solution protects containers running on AWS, Azure, and on-premises platforms, including Docker, AWS Elastic Container Service (ECS), Kubernetes, AWS Elastic Beanstalk, and CoreOS, delivering seamless and effective defense against evolving cyber threats.
What is the Role of a Network IDS?
NIST defines an IDS as “a security service that monitors and analyzes network or system events to detect and provide real-time or near-real-time warnings of unauthorized attempts to access system resources.” An IDS primarily examines internal network traffic to identify suspicious or malicious activity, enabling it to detect attacks that bypass the firewall or originate from within the network.
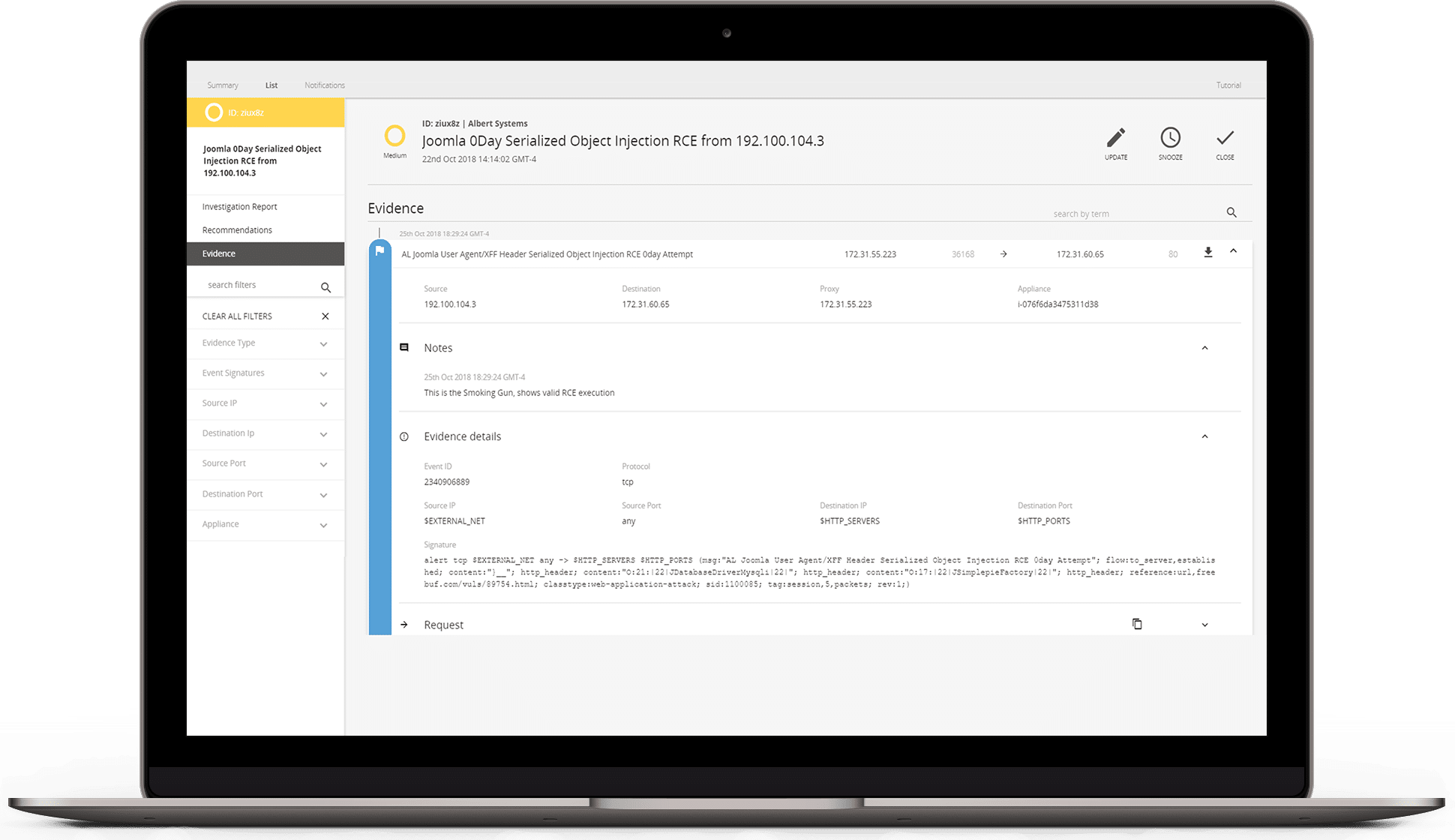
A network IDS is critical for securing your network as it allows you to detect and respond to malicious traffic. It can immediately alert your team of potential attacks or network intrusions. A network IDS also continuously monitors all inbound, outbound, and internal traffic, analyzing data flows between systems within the network. When suspicious activity or recognized threats are detected, the IDS triggers immediate alerts, empowering the IT team to respond swiftly, investigate thoroughly, and take decisive action to block or mitigate an attack before it causes damage.
The Benefits of a Managed Network IDS
We relentlessly hunt for hidden security threats in your network traffic. Unreliable IDS alerts drain your team’s time, allowing real breaches to go undetected for an average of 277 days. With Alert Logic’s IDS, our expert team manages the solution and delivers actionable insights so you can respond to threats with confidence and precision:
- Achieve rapid security monitoring in minutes with pre-built automated deployment
- Effortlessly scale with low-impact agents that self-configure, self-register, and self-deregister — ensuring seamless, no-touch support for auto-scaling environments
- Secure your network with deployed agents that encrypt and transmit all ingress, egress, and lateral traffic to the Alert Logic backend for advanced threat processing
- We compare your network traffic with over 17,000 active IDS signatures that detect a wide array of malicious activity and attack methods, including exploits in app stack components, and attack methods included in the OWASP Top 10
- 24/7 security monitoring, expert incident analysis, and live notifications of critical attacks by security analysts in our global SOC
Harness Your IDS Data for Proactive Network Security
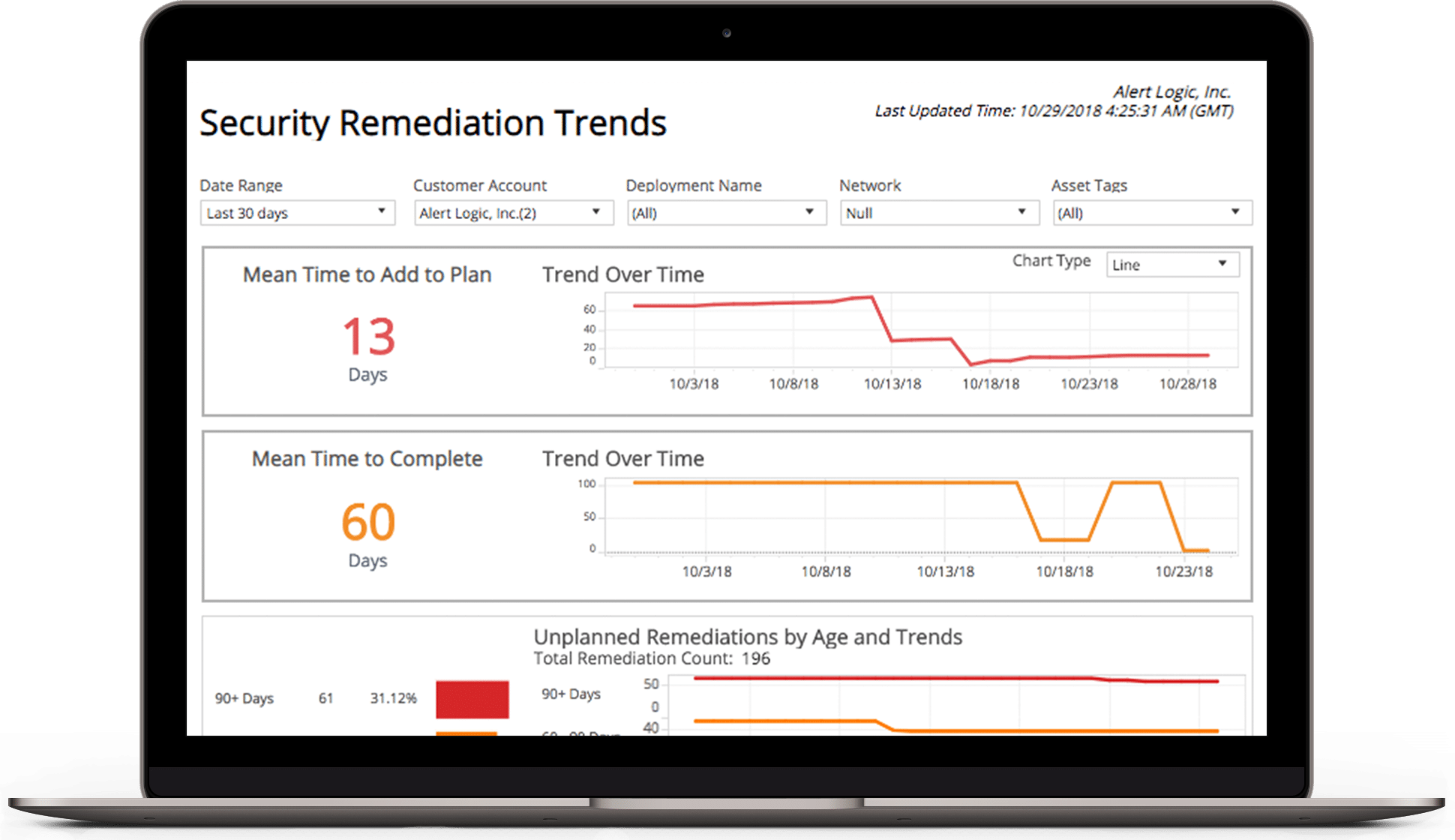
- Always-on monitoring and scanning, advanced analytics combined with machine learning provide a holistic view of your environment so you can detect network intruders faster
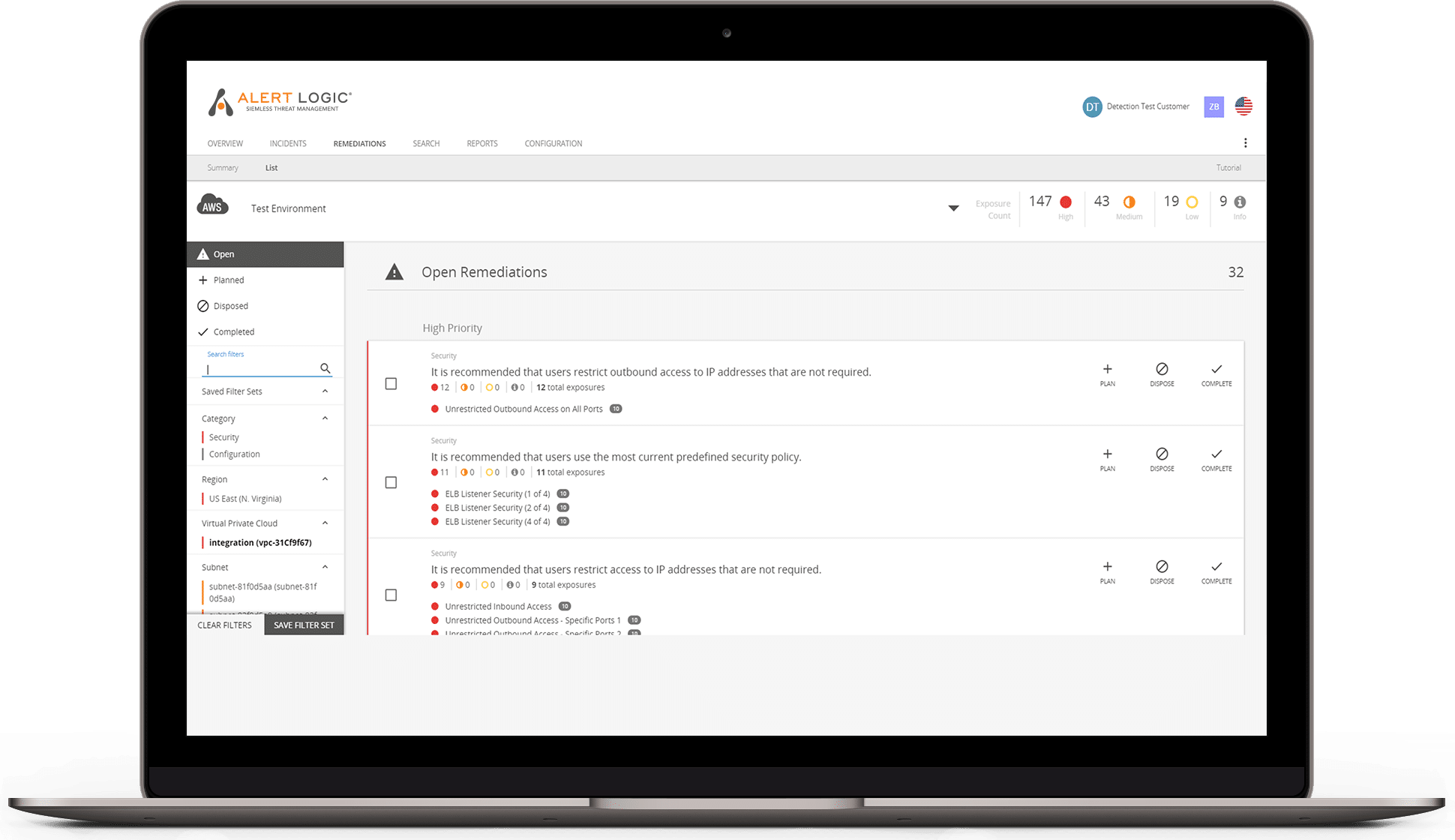
- Receive pre-built or ad hoc reports that include risk levels, threat details, potential impact, and detailed remediation recommendations
- Filter or search on asset groups, hosts, services, open ports, or specific vulnerabilities to find and address an emerging threat